PBR Configuration with Match Statements [CCNP ENTERPRISE]
Ever found yourself in a situation where you wanted to override the default routing decisions of your router? Maybe route specific traffic over a particular WAN link? That’s where Policy-Based Routing (PBR) becomes your best friend.
In my experience training hundreds of engineers, I’ve seen PBR often misunderstood or underutilized. Most folks stick with traditional routing protocols, but what if you could make your router act based on policies you define — based on source IPs, destination IPs, protocols, or even port numbers? Today, we’re going to simplify PBR with Match Statements and walk through it like a real-world engineer — not just theory, but labs, use cases, CLI, and troubleshooting tips.
Let’s begin this journey and master one of the most powerful tools in your networking toolkit.
Table of Contents
Theory in Brief: What is PBR?
Policy-Based Routing (PBR) is a technique used to make routing decisions based on policies set by the network admin, rather than just destination-based routing as done by traditional protocols.
With PBR, you can:
- Override the routing table
- Define granular forwarding rules
- Route traffic based on source IP, destination IP, DSCP, ACL, etc.
- Achieve load balancing, selective path routing, and more
How Does It Work?
PBR uses route maps with match and set statements. You “match” specific traffic criteria (like source IP, protocol, or ACL), and then “set” what you want to do with that matched traffic — like forwarding to a specific next-hop IP.
PBR is implemented on incoming interfaces — so it checks each packet as it enters the router.
Comparison: Pros, Cons, and Key Differences
| Feature | Description |
|---|---|
| Traditional Routing | Based on destination IP only |
| PBR Routing | Can match source IP, protocol, interface, etc. |
| Flexibility | High – route traffic exactly how you want |
| Use Cases | Load balancing, traffic engineering, policy control |
| Performance Impact | Slight CPU impact – applies policy on a per-packet basis |
| Configuration Complexity | Medium – involves ACLs and route maps |
| Troubleshooting Difficulty | Medium – logs and counters are needed |
Essential CLI Commands – Configure and Verify PBR
| Task | Command Example |
|---|---|
| Create ACL to match traffic | ip access-list extended PBR_ACLpermit ip 192.168.1.0 0.0.0.255 any |
| Create Route-map with match | route-map PBR_POLICY permit 10match ip address PBR_ACLset ip next-hop 10.1.1.1 |
| Apply route-map on interface | interface GigabitEthernet0/1ip policy route-map PBR_POLICY |
| Verify PBR is working | show route-mapshow ip policyshow access-lists |
| Debug PBR live traffic | debug ip policydebug ip packet |
| Check interface traffic stats | show interfaces GigabitEthernet0/1 |
Real-World Use Case
| Scenario | Description |
|---|---|
| Company with dual ISPs | Route corporate traffic (source: 192.168.1.0/24) via ISP-1 (10.1.1.1), and guest traffic (192.168.2.0/24) via ISP-2 (10.2.2.2) |
| Business Need | Save cost by routing non-critical guest traffic via cheaper ISP |
| Solution | Use ACLs and route-maps with PBR to forward based on source subnets |
| Benefit | Granular control of traffic, cost optimization, and improved performance |
Small EVE-NG Lab – Test and Understand
LAB DIAGRAM:
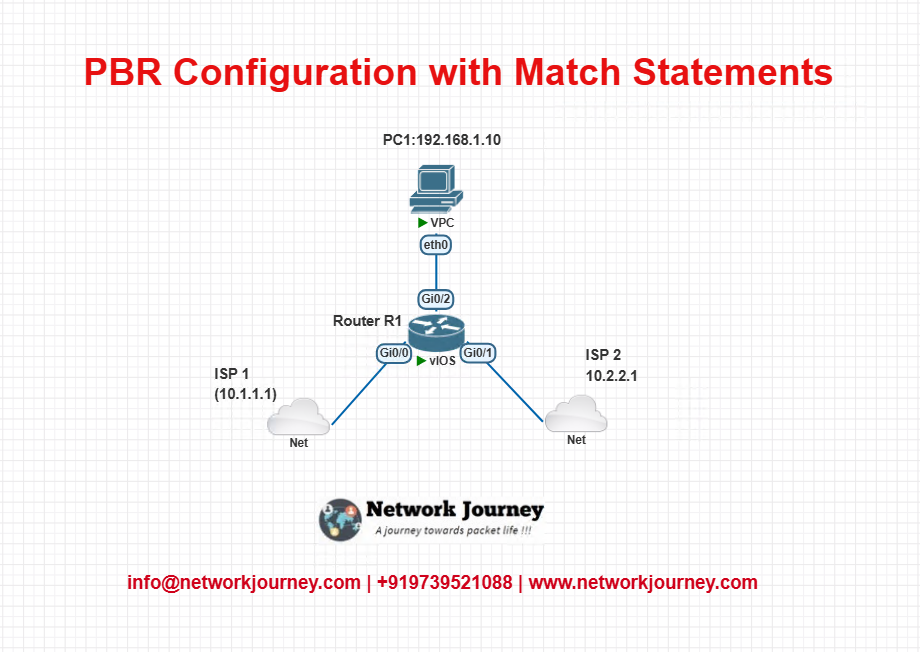
CLI CONFIGURATIONS
Step 1: Create ACL
ip access-list extended CORP_TRAFFIC
permit ip 192.168.1.0 0.0.0.255 any
Step 2: Create Route-Map
route-map CORP_POLICY permit 10
match ip address CORP_TRAFFIC
set ip next-hop 10.1.1.1
Step 3: Apply on Interface
interface GigabitEthernet0/1
description Link to LAN
ip policy route-map CORP_POLICY
Step 4: Add Default Routes (Backup Path)
ip route 0.0.0.0 0.0.0.0 10.2.2.1
Verification
show route-map
show ip policy
debug ip policy
Troubleshooting Tips
| Issue | Tip / Command |
|---|---|
| Policy not applying | Check show ip policy to ensure it’s attached on correct interface |
| ACL not matching traffic | Use show access-lists to see if packets hit ACL |
| Incorrect next-hop | Ensure the set ip next-hop is reachable |
| No effect from PBR | Check default route is not overriding policy |
| High CPU or lag | Avoid overusing PBR on high-throughput interfaces |
Most common FAQs
1. What is Policy-Based Routing (PBR)?
Answer:
PBR is a technique that allows you to override the default routing behavior by forwarding traffic based on custom match conditions (like source IP, destination IP, or protocol), instead of the routing table (RIB).
It is used when you want custom routing policies like:
- Sending certain traffic through a specific ISP.
- Redirecting traffic to a firewall or WAN optimizer.
- Enforcing QoS-based path selection.
2. What are match statements in PBR and why are they important?
Answer:
Match statements define the conditions that packets must meet to trigger PBR. You can match:
- Source IP or subnet
- Destination IP
- Protocol
- IP DSCP/precedence
- ACLs
Example:
route-map PBR-EXAMPLE permit 10
match ip address 101
This tells the router: “If a packet matches ACL 101, apply the PBR action.”
3. What actions can be applied to matched traffic in PBR?
Answer:
Once a packet matches the condition, PBR can apply actions like:
- Set next-hop IP address
- Set default next-hop
- Set interface
- Set IP precedence/DSCP
Example:
route-map PBR-EXAMPLE permit 10
match ip address 101
set ip next-hop 192.168.1.1
This routes matched traffic through 192.168.1.1, ignoring the regular routing table.
4. How do I apply a PBR policy to an interface?
Answer:
Use the ip policy route-map command under the incoming interface:
interface GigabitEthernet0/0
ip policy route-map PBR-EXAMPLE
PBR is applied to incoming traffic only, not outbound.
5. What’s the difference between set ip next-hop and set interface?
Answer:
| Action | Behavior |
|---|---|
set ip next-hop | Routes the packet to the specified next-hop IP if it’s reachable. |
set interface | Forwards the packet out a specific interface, ignoring next-hop IP. |
set ip next-hop is safer and more common. set interface can break things if not used carefully.
6. Can I match multiple conditions in a single route-map?
Answer:
Yes. You can match combinations like:
route-map PBR-MULTI permit 10
match ip address ACL1
match length 100 1500
match ip dscp 46
set ip next-hop 10.1.1.1
This allows fine-grained control — only traffic that meets all conditions will be redirected.
7. How do I match traffic from a specific subnet in PBR?
Answer:
Use a standard or extended ACL:
access-list 101 permit ip 192.168.10.0 0.0.0.255 any
route-map PBR-SUBNET permit 10
match ip address 101
set ip next-hop 10.0.0.1
This forwards all traffic from 192.168.10.0/24 via 10.0.0.1, ignoring routing table decisions.
8. What happens if the next-hop is unreachable in PBR?
Answer:
If the set ip next-hop address is unreachable:
- PBR fails silently and the router falls back to regular routing (RIB lookup).
- Unless you use
set ip default next-hop, which only works if the normal route fails.
For failover, always ensure the next-hop is reachable via connected interface or use tracking.
9. How can I verify if PBR is working on a Cisco router?
Answer:
Use these commands:
show route-map
show ip policy
show ip access-lists
debug ip policy
Also, use ping and traceroute from test devices to confirm the path is being altered. You should see traffic following the PBR-defined path instead of the default route.
10. Can you provide a full working example of a basic PBR configuration?
Answer:
Match traffic from 192.168.10.0/24
access-list 101 permit ip 192.168.10.0 0.0.0.255 any
! Define route-map
route-map PBR-TEST permit 10
match ip address 101
set ip next-hop 10.0.0.1
! Apply on interface
interface GigabitEthernet0/0
ip policy route-map PBR-TEST
In this setup:
- Traffic from 192.168.10.0/24 entering G0/0 will be routed to 10.0.0.1, bypassing normal routing decisions.
YouTube Link
Watch the Complete CCNP Enterprise: PBR Configuration with Match Statements Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement PBR Configuration with Match Statements is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![PBR Configuration with Match Statements [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/PBR-Configuration-with-Match-Statements-CCNP-ENTERPRISE-.png)

![[Day #18 Pyats Series] Building test case hierarchy with Section, CommonSetup using pyATS for Cisco](https://networkjourney.com/wp-content/uploads/2025/07/Building-test-case-hierarchy-with-Section-CommonSetup-using-pyATS-for-Cisco.png)
