QoS Diagnose & Fix Network Performance Issues [CCNP Enterprise]
If you’ve ever hit the panic button because your VoIP calls are choppy or your video stream froze mid-presentation, I feel your pain. Just this morning, I was on a call that sounded like we were underwater—definitely not the crisp audio I expect! That’s when QoS troubleshooting becomes your superhero cape. In this guide, we’ll walk through real-world scenarios, CLI tactics, and lab drills so you can swiftly identify and resolve performance glitches. Let’s tackle these issues head-on, shall we?
Table of Contents
Theory in Brief
What is QoS Troubleshooting?
QoS (Quality of Service) troubleshooting is the process of diagnosing and resolving issues related to traffic prioritization, queuing, classification, or marking in your network. It helps prevent dropped packets, latency spikes, and jitter—especially during congestion.
Why It Matters
In multi-traffic networks—where voice, video, cloud apps, and file transfers coexist—bandwidth competition is real. QoS ensures critical applications get the facility they need. When it doesn’t work, users notice. And they complain. And you fix it.
Key Steps in Troubleshooting
- Detect the issue — collect symptoms like jitter or packet loss.
- Isolate components — queuing, policing, shaping, marking.
- Use CLI tools — show, debug, clear stats, etc.
- Observe metrics — match rates, drops, queue depth.
- Adjust policies — tweak limiting, buffering, priority allocations.
- Validate — re-run tests, observe behavior improvements.
Best Practices
- Start simple: match stats and packet naming.
- Work systematically: rule out one component at a time.
- Use lab scenarios: replicate issues, test fixes before deploying.
- Monitor continuously: QoS isn’t “set and forget.” It evolves with traffic.
Summary / Comparison / Pros & Cons
| Scenario | Symptoms | Likely Cause | Best CLI Tool | Fix Strategy |
|---|---|---|---|---|
| Voice jitter/delay | Choppy audio, call quality hits | LLQ not assigned or too small | show policy-map interface | Add LLQ, increase priority percentage |
| Bulk traffic hogging link | Slow responses, files never end | Lack of policing/shaping | show queueing interface, show policy-map | Shape or police bulk class, limit bursts |
| Unexpected drops | Missing or high drop counters | WRED thresholds too low | show queueing interface, show wred | Tune WRED thresholds |
| DSCP/marking ignored | No DSCP tags in reports | Trust boundary misconfigured | show mls qos interface trust, show policy-map interface | Set correct trust on devices |
| Packet misclassification | Wrong packets in wrong queue | Class-map ACL or match statements off | debug qos packet class-map | Correct ACLs or DSCP matches } |
| Shaping causing lag | Increased latency under load | Excessive buffer use | show policy-map interface, show queueing interface | Reduce burst size, tweak shape rate |
| LLQ starving others | Other traffic slow or dropped | LLQ too large or no bandwidth share | show policy-map interface, show queueing interface | Add bandwidth to class-default |
| Ingress drops | Packets dropped as ingress | Policer misconfigured | show policy-map interface, show class-map | Adjust policer rate or convert to shaping |
| Spikes during bursts | Periodic packet loss | Not enough buffer or misweighted queue | show queueing interface, show class-map | Reallocate buffers or adjust WFQ weights |
| QoS not working at edge | End-to-end issues, no marking | Service-policy not applied on interface | show running-config, show policy-map interface | Apply the correct service-policy |
Essential CLI Commands
| Task | Command Example | Purpose |
|---|---|---|
| Show interface policy | show policy-map interface Gi0/1 | View matched traffic and queue stats |
| Inspect queue state | show queueing interface Gi0/1 | View queue utilization, drops |
| Check WRED parameters | show wred interface Gi0/1 | Examine WRED thresholds |
| Debug classification | debug qos packet class-map VOICE | See which class-map is matching live packets |
| Show trust configuration | show mls qos interface Gi0/2 trust | Validate DSCP/CoS trust setup on switch interfaces |
| View globally configured QoS maps | show mls qos maps | Check DSCP-to-CoS and mark settings |
| Show class-map definitions | show class-map VOICE | Confirm classification criteria |
| Clear policy counters | clear policy-map interface Gi0/1 counters | Reset stats for troubleshooting |
| Show shaping statistics | show policy-map interface Gi0/1 | Includes shaping/policing rates |
| Show port queue use | show queuing interface Gi0/1 | Displays per-queue usage and drops |
Real‑World Use Case Scenarios
| Use Case | Problem Description | QoS Misconfiguration | Solution | Outcome |
|---|---|---|---|---|
| Branch Voice Failures | Scaling up VOIP served poor call quality | LLQ not implemented, default queue used | Add priority 20 for VOICE in policy-map | Jitter stabilized, calls improved |
| Daily Backup Disruption | Daily backups slow business tools | No shaping, backup hogged all bandwidth | Implement shape average for backup class | Backups run off-hours, business unaffected |
| Sudden Drops at Edge | Intermittent application drops noticed across branch link | Misaligned WRED thresholds, early drops | Adjust WRED on egress interface | Packet throughput normalized, drops resolved |
| DSCP Not Preserved | Core saw only default DSCP even though edge marked packets | Trust removed on trunk port | Apply mls qos trust dscp on trunk | DSCP preserved, classification improved |
| Inaccurate Classification | Bulk traffic ended up in VOICE queue | Class-map used wrong ACL-DSCP match | Correct ACL and class-map to match actual traffic | Bulk moved to right queue, voice decongested |
Small EVE‑NG Lab Scenario
Lab Diagram
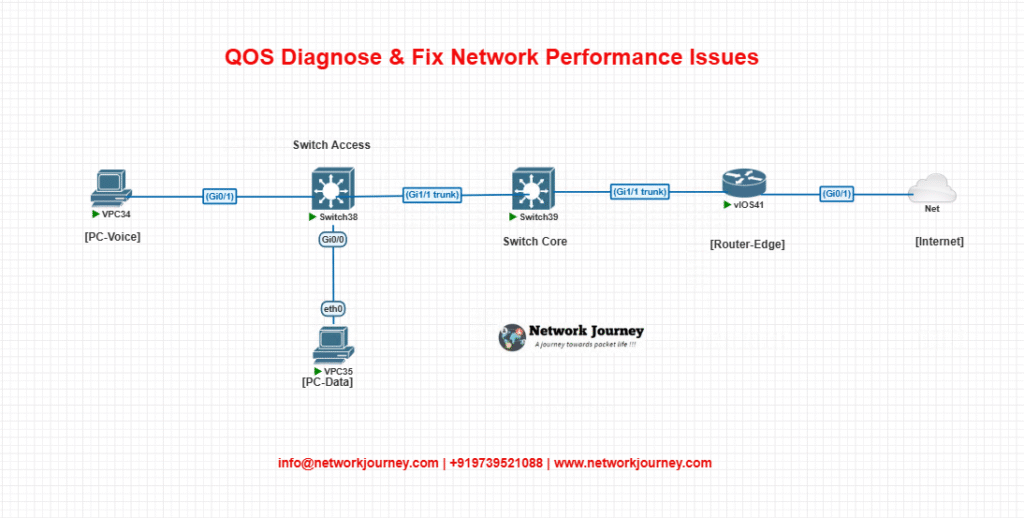
- Switch-Access: Contains Voice (CoS trust) and Data (no trust)
- Switch-Core: DSCP trust trunk link
- Router-Edge: Applies QoS policy (LLQ, policing, WRED) on egress
CLI Configuration
Switch-Access
interface Gi0/1 switchport mode access switchport access vlan 10 mls qos trust cos interface Gi0/2 switchport mode access switchport access vlan 20 mls qos trust none interface Gi1/1 switchport mode trunk mls qos trust dscp
Router-Edge
class-map match-any VOICE match ip dscp ef class-map match-any BULK match access-group 101 access-list 101 permit ip any any policy-map EDGE-QOS class VOICE priority 2000000 class BULK shape average 5000000 class class-default fair-queue random-detect interface Gi0/1 service-policy output EDGE-QOS
Troubleshooting Tips
| Issue | Likely Cause | CLI Tips for Diagnosis | Recommended Fix |
|---|---|---|---|
| Voice jitter under load | LLQ not assigned or too small | show policy-map interface, show queueing interface | Add/update LLQ and priority percentage |
| Backup traffic dropping others | No shaping or LLQ misconfiguration | show policy-map, debug qos packet | Add shaping for backup class |
| Drops during queues overflow | WRED thresholds too aggressive | show queueing interface, show wred | Loosen WRED thresholds or change queue fairness |
| DSCP tags missing mid-network | Trust misconfigured on switch or trunk | show mls qos interface, show mls qos maps | Apply correct trust mode on relevant interfaces |
| Wrong traffic in wrong queue | Class-map ACL or match incorrect | debug qos packet class-map, show class-map | Correct class-map or ACL logic |
| Poor throughput post-policing | Policer threshold or burst definined too low | show policy-map interface, show policy-map interface class BULK | Increase CIR or convert to shaping |
| High latency because of shaping | Buffer causing delays | show policy-map interface, show queueing interface | Reduce burst size or use less aggressive shaping |
| Service-policy missing on interface | Applied to wrong interface/direction | show running-config, show policy-map interface | Apply to correct interface and direction |
| Counters not updating | Misplaced service-policy or inactive class-map | show policy-map interface, show class-map | Correct direction or add missing policy/class-map |
| New traffic not matching policy | Missing or improper ACL/DSCP in class-map | show class-map, debug qos packet class-map | Update classification logic to include relevant traffic |
FAQs
1: What are the most common causes of network performance issues in enterprise environments?
Answer:
The most common causes include:
- Congestion on WAN or uplink interfaces due to bandwidth overuse.
- Lack of QoS policies, leading to critical traffic (like VoIP or video) being treated as best effort.
- Misconfigured QoS policies, such as incorrect class-maps or untrusted markings.
- Hardware limitations like buffer exhaustion on switches or routers.
- High CPU or memory usage on routing devices affecting packet forwarding.
Diagnosing starts with identifying where the symptoms appear—user endpoints, edge routers, or core switches—and then drilling into traffic statistics.
2: How can I detect high latency or jitter affecting voice and video traffic?
Answer:
Latency and jitter often manifest as:
- Choppy audio during VoIP calls.
- Pixelated or freezing video during conferencing.
Use the following tools: pingandtracerouteto find latency spikes.- IP SLA (on Cisco) to measure jitter and response time.
- Wireshark to view packet inter-arrival times and jitter variation.
show policy-map interfaceon routers to see if voice traffic is being prioritized and whether it’s dropping.
Ensure that voice/video is in a Low Latency Queue (LLQ) and that the queue isn’t experiencing drops.
3: What CLI commands can I use to quickly identify performance bottlenecks on Cisco devices?
Answer:
Here are powerful commands for diagnosis:
show interfaces– Reveals input/output errors, drops, and load.show policy-map interface– Displays traffic classes, drops, queue stats.show platform hardware qos interface [interface] queue stats– On some platforms, shows queue utilization in detail.show queueing interface– Displays congestion stats.debug qos packet– Debugs real-time packet classification.
Use these to confirm if bandwidth limits are exceeded or queues are full.
4: How do I confirm if QoS marking is preserved end-to-end across the network?
Answer:
Use the following to verify:
show mls qos interfaceon switches to see trust state.- Packet capture (e.g., Wireshark or SPAN) to view DSCP values.
show policy-map interfaceto see if packets are classified correctly based on DSCP.
Markings may be stripped or altered at switches if trust boundaries are misconfigured. Ensure mls qos trust dscp is enabled on trunk ports and VoIP-connected access ports.
5: What are trust boundaries, and how do they impact QoS?
Answer:
A trust boundary defines where you choose to accept or overwrite QoS markings from devices. Typically:
- Trusted: Cisco IP Phones, trusted routers.
- Untrusted: End-user devices, laptops.
If a device is outside the trust boundary, its markings are ignored or reset. Misconfigured trust can result in critical traffic being marked as best effort, affecting performance.
Use:
mls qos trust dscp
on trusted interfaces, and leave it off where QoS should be assigned by the switch/router.
6: How can I identify whether traffic is being dropped due to misconfigured QoS?
Answer:
Drops due to QoS often show up in:
show policy-map interface– Check for high drop counters.show queueing interface– Reveals queue lengths and drops.- LLQ overuse – If voice is dropping, LLQ might be too small.
- Policing misconfiguration – Can cause packets to be dropped unnecessarily.
If a class has a high drop count and match rate, verify the bandwidth allocation, policing, or shaping settings.
7: My backup traffic is affecting VoIP calls. How do I fix this?
Answer:
The backup traffic likely uses too much bandwidth, starving voice. Solutions:
- Classify backup traffic in a separate class-map.
- Apply shaping (e.g.,
shape average) to limit its bandwidth. - Ensure voice is in a priority queue (
prioritycommand).
Example:
class-map match-any BACKUP match access-group 101 policy-map WAN-QOS class VOICE priority 2000 class BACKUP shape average 500000
Apply the policy to the WAN egress interface.
8: What tools can simulate network issues for testing QoS policies?
Answer:
For lab testing:
- EVE-NG or GNS3: Simulate a full Cisco topology.
- iPerf or ping flood: Simulate traffic loads.
- Cisco IP SLA: Emulates delay-sensitive traffic like voice.
- D-ITG or Nping: Send specific types of packets with custom DSCP.
These tools help verify QoS marking, queuing behavior, and shaping/policing effects before live deployment.
9: Why isn’t my QoS policy matching any traffic?
Answer:
Possible causes:
- Wrong ACL or class-map criteria.
- Service-policy not applied to the correct interface or direction.
- DSCP or CoS mismatches.
- Traffic arrives unmarked or marked differently than expected.
Use debug qos packet and show class-map to verify:
- Packet headers.
- Match conditions.
- Whether the policy is active.
Always test matches with a real or simulated traffic source.
10: How often should I review or adjust my QoS policies?
Answer:
QoS policies should be reviewed quarterly or when:
- You add new applications (like new VoIP systems or video tools).
- Users complain of performance degradation.
- Link utilization changes (e.g., upgrading from 100 Mbps to 1 Gbps).
- SLA compliance reporting shows jitter, delay, or loss.
Use NetFlow, SNMP monitoring, and CLI tools to collect performance data and adjust policies as needed. QoS is dynamic—adapt as traffic patterns evolve.
YouTube Link
Watch the Complete CCNP Enterprise: QOS Diagnose & Fix Network Performance Issues Lab Demo & Explanation on our channel:
Final Takeaways
Understanding how to differentiate and implement QOS Diagnose & Fix Network Performance Issues is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![QOS Diagnose & Fix Network Performance Issues [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/QOS_Diagnose_Fix-Network-Performance-Issues_networkjourney.png)

![Virtual Network Functions (VNFs) – The Future of Flexible Networking [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/Virtual-Network-Functions-_VNFs-–-The-Future-of-Flexible-Networking-_networkjourney.png)
![Ultimate Comparison: NetFlow vs sFlow – Insights [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Ultimate-Comparison_NetFlow-vs-sFlow-–-Insights_networkjourney.png)