Security Zones Explained: From Flat Networks to Fortresses [CCNP ENTERPRISE]
Let’s be honest. At some point, we’ve all created a flat network with just a few VLANs and thought — “Yeh toh kaafi secure hai.” Until… a misconfigured ACL or open port lets someone pivot from the user segment to your server VLAN — and suddenly, your core gets compromised.
This happened to one of my students in a live data center. They had firewalls, VLANs, even ACLs, but no zoning. Once we fixed their security zones and policies, lateral movement attacks stopped immediately.
Security zones aren’t just a “next-gen firewall” feature — they’re an essential design principle every engineer should master.
In this guide, I’ll take you from theory to CLI to EVE-NG lab — so you can implement security zones in your own environment confidently.
Table of Contents
Theory in Brief
What are Security Zones?
Security zones are logical groupings of interfaces or networks with similar security levels.
They define how traffic is allowed or restricted between areas like:
- Inside (trusted)
- Outside (untrusted)
- DMZ (semi-trusted)
- VPN zones
- Guest zones
Instead of just using ACLs or VLANs, zones help you define policies between groups, making security both scalable and understandable.
Why Use Zones?
Without zones, managing access is like handling a 100-way intersection with traffic lights on each street — chaos. Zones abstract complexity by creating lanes.
You create zone-based policies such as:
- “Allow DMZ to talk to Database only on port 3306”
- “Deny Guest access to Inside zone”
This approach gives clear segmentation, policy consistency, and layered defense — especially critical in firewalls like Cisco ASA, Palo Alto, Fortigate, and even SD-WAN.
Where Are Zones Applied?
Zones are typically applied in:
- Firewalls (Zone-Based Firewall on Cisco IOS/ASA, Fortigate, Palo Alto)
- Routers with ZBFW
- SD-WAN edge devices
- Some L3 switches
Even cloud vendors (AWS Security Groups, Azure NSGs) use zone-like policy controls.
Key Design Considerations
- Least Privilege: Start with Deny All and allow only what’s needed
- Consistency: Apply same rules for similar zones across locations
- Logging: Log inter-zone traffic for auditing
- Fail-Open vs Fail-Close: Decide how devices behave on failover
Security Zone Comparison
| Zone Type | Trust Level | Typical Use | Can Access |
|---|---|---|---|
| Inside | High | Core LAN, trusted users | Internet, DMZ, limited guest |
| Outside | Low | Internet or ISP edge | Limited inbound (NATed) only |
| DMZ | Medium | Public-facing servers (web, mail) | Inside (controlled), Outside |
| VPN Zone | Medium | Remote workers | Inside (based on policy) |
| Guest | Very Low | BYOD, visitors | Only Internet (No internal) |
CLI Commands (Cisco IOS ZBFW Example)
| Task | CLI Command |
|---|---|
| Enable ZBFW | zone security INSIDEzone security OUTSIDE |
| Assign interface to zone | interface Gig0/1zone-member security INSIDE |
| Define class map | class-map type inspect match-any CM_HTTPmatch protocol http |
| Define policy map | policy-map type inspect PM_INSIDE_TO_OUTSIDEclass CM_HTTPinspect |
| Apply policy to zone pair | zone-pair security ZP_INSIDE_OUTSIDE source INSIDE destination OUTSIDEservice-policy type inspect PM_INSIDE_TO_OUTSIDE |
| View policy config | show zone securityshow policy-map type inspect zone-pair |
| Debug traffic | debug policy-map type inspect |
Real-World Use Cases
| Scenario | Problem | Solution (Zone-Based) |
|---|---|---|
| Flat LAN network | No segmentation, easy lateral movement | Create Inside, DMZ, Guest zones |
| Server in same VLAN as users | Direct access to databases/web apps | Place servers in DMZ with tight ACLs |
| Branch office access to cloud only | Unnecessary access to corporate LAN | VPN zone limited to Internet access only |
| IoT Devices in office LAN | Insecure devices on critical network | Create IoT Zone, restrict to Internet |
| BYOD devices getting DHCP from LAN | Data leak risk | Create Guest Zone with Internet-only rule |
Lab: Security Zones in Action
Topology Diagram (Simplified)
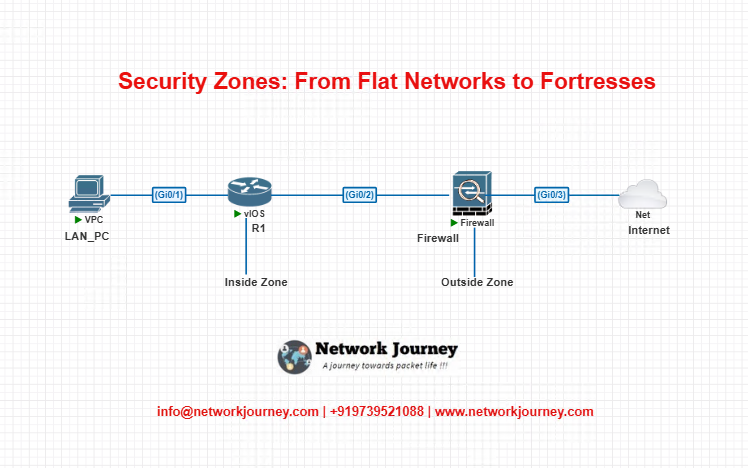
LAB STEPS (Cisco IOS Firewall – Zone Based)
- Create Zones
zone security INSIDE
zone security OUTSIDE
- Assign Interfaces to Zones
interface Gi0/1
zone-member security INSIDE
interface Gi0/2
zone-member security OUTSIDE
- Create Class Map
class-map type inspect match-any WEB_TRAFFIC
match protocol http
match protocol https
- Create Policy Map
policy-map type inspect POLICY_INSIDE_OUT
class WEB_TRAFFIC
inspect
class class-default
drop
- Create Zone Pair
zone-pair security ZP_IN_OUT source INSIDE destination OUTSIDE
service-policy type inspect POLICY_INSIDE_OUT
- Test Traffic
From LAN PC, browse to http://8.8.8.8 — it should pass.
Try SSH — it should be blocked unless added in class-map.
Troubleshooting Tips
| Symptom | Likely Cause | Resolution |
|---|---|---|
| All traffic blocked | Policy not applied or zones misconfigured | Check zone-member, zone-pair, and policies |
| Ping not working | ICMP not matched in class-map | Add ICMP to class-map or allow in ACL |
| Debug shows drop | Implicit drop by class-default | Add specific matches or separate policy |
| ACL not effective | ZBFW overrides ACLs | Apply rules via policy maps |
| No logs seen | Logging not enabled | Use log keyword or monitor logging |
Frequently Asked Questions
What is the purpose of security zones in a network?
Answer:
Security zones help segment the network into logical areas with defined trust levels. The main purpose is to:
- Isolate critical systems from less trusted users or networks
- Control and monitor traffic between different parts of the network
- Enforce least privilege policies using zone-based access controls
- Improve visibility, compliance, and incident response
- Reduce the attack surface by limiting lateral movement
2: How do security zones differ from VLANs or subnets?
Answer:
- VLANs/Subnets are Layer 2/Layer 3 constructs used to segment traffic physically or logically.
- Security Zones, on the other hand, are policy-based logical groupings that define what traffic is allowed or denied between network areas.
You can think of zones as an additional security policy layer over VLANs or subnets.
3: Is it mandatory to assign every interface to a zone?
Answer:
Yes, if you’re using Zone-Based Firewall (ZBFW) on Cisco IOS or a similar security platform. Any interface not assigned to a zone:
- Will not pass traffic to/from zone members
- Could become an unmonitored or vulnerable interface
- Might not participate in policy enforcement
To ensure proper filtering, every active interface should be assigned to a zone.
4: What happens if I don’t define a zone-pair between two zones?
Answer:
If no zone-pair exists between two zones:
- Traffic between them is implicitly denied
- No policy will be enforced
- Even permitted protocols will not function
Solution: Always create a zone-pair and policy for any inter-zone communication.
5: Can I allow some traffic and block others between zones?
Answer:
Yes. With policy maps and class maps, you can:
- Match specific protocols (e.g., HTTP, SSH, ICMP)
- Permit or inspect some while denying others
- Add logging and connection tracking if needed
This gives you granular control over what’s allowed between zones.
6: Is traffic allowed between interfaces in the same zone?
Answer:
Yes. By default, intrazone traffic is allowed unless explicitly denied.
This means:
- Devices in the same zone (e.g., INSIDE) can communicate freely
- It reduces complexity for same-trust-level devices
- Still, logging and inspection can be applied manually if required
7: How do I design effective security zones?
Answer:
Use the Principle of Least Privilege and follow these guidelines:
- Group interfaces with similar trust levels
- Create zones for:
- Inside (core users, servers)
- Outside (internet)
- DMZ (public-facing apps)
- VPN (remote users)
- Guest (BYOD, visitors)
- IoT (non-compliant or smart devices)
- Define clear policies between zones
- Use naming conventions like
ZP_INSIDE_DMZ,ZP_GUEST_OUTSIDE
8: Can I use ACLs with security zones?
Answer:
Yes, but:
- In most firewall or router platforms (like Cisco IOS ZBFW), zone policies take precedence over ACLs
- ACLs can still be used for fine-grained control inside a zone or between specific subnets
- It’s recommended to use policy maps for inter-zone filtering, and ACLs for intra-zone or host-level rules
9: How can I monitor or troubleshoot inter-zone traffic?
Answer:
Use these tools and commands:
- Enable debugging: bashCopyEdit
debug policy-map type inspect all - Check applied policies: bashCopyEdit
show policy-map type inspect zone-pair show zone security - Log matches: Use
logkeyword in class-map or policy-map - Wireshark/tcpdump: Use on test clients for traffic validation
10: Are security zones supported only on firewalls?
Answer:
No. Security zones are supported on multiple platforms:
- Cisco Routers: ZBFW with CLI
- Cisco ASA/FTD: ASA policies use zones
- Palo Alto: Zone-based by design
- FortiGate: Interfaces are grouped into zones
- SD-WAN: Zones used for segmentation
- Cloud: AWS Security Groups and Azure NSGs act like zones
So the concept is vendor-agnostic, even if the implementation varies.
YouTube Link
Watch the Complete CCNP Enterprise: Security Zones Explained: From Flat Networks to Fortresses Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Security Zones Explained: From Flat Networks to Fortresses is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Security Zones Explained: From Flat Networks to Fortresses [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-security-zone.jpg)
![Configuring QoS on Cisco Devices: Boost Performance & Ensure Traffic Priority [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Configuring-QoS-on-Cisco-Devices_Boost-Performance_Ensure-Traffic-Priority_networkjourney.png)
![How Do Bridge Domains and EPGs Work Together in Cisco ACI?[CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/How-Do-Bridge-Domains-and-EPGs-Work-Together-in-Cisco-ACI_networkjourney.png)
![EIGRP for IPv6 – Routing Smarter in the Next-Gen Network Era [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/EIGRP-for-IPv6-–-Routing-Smarter-in-the-Next-Gen-Network-Era_networkjourney-1.png)