Ticket#10 – NAT Overload Failure: Why Users Couldn’t Access the Internet – A Real Fix [CCNP ENTERPRISE]
Table of Contents
Problem Summary
In a mid-sized enterprise, users across VLANs suddenly reported that they couldn’t browse the internet or access external services. While internal services like file sharing and internal DNS were operational, anything beyond the firewall was unreachable.
Symptoms Observed
- Clients couldn’t reach external IPs (e.g.,
8.8.8.8,google.com) - Continuous timeouts in
ping,tracerouteto internet - Default gateway was reachable
- DNS resolution was working for some, but responses were not consistent
- No issues in internal VLAN-to-VLAN communication
- Access Layer switches and Core showed normal CPU/memory usage
- Logs showed NAT translation failures
Root Cause Analysis
Initial checks revealed:
- The internet-facing interface was up/up
- IP routing was working, default route pointed to ISP
- NAT configuration was present, but NAT table was not populating
- Overload keyword was missing from the
ip nat inside sourcestatement - ACL tied to NAT did not include newer subnets
- Translation logs were empty → No NAT means no return traffic
The Fix
After pinpointing NAT as the root cause, the following steps were taken:
Step 1: Fix NAT Configuration
conf t
ip access-list standard NAT_ACL
permit 192.168.10.0 0.0.0.255
permit 192.168.20.0 0.0.0.255
ip nat inside source list NAT_ACL interface GigabitEthernet0/1 overload
Step 2: Define Interfaces
interface GigabitEthernet0/0
ip nat inside
interface GigabitEthernet0/1
ip nat outside
Step 3: Clear Stale NAT Translations
clear ip nat translation *
EVE-NG Lab Topology
Here’s a simplified lab diagram to replicate the issue:
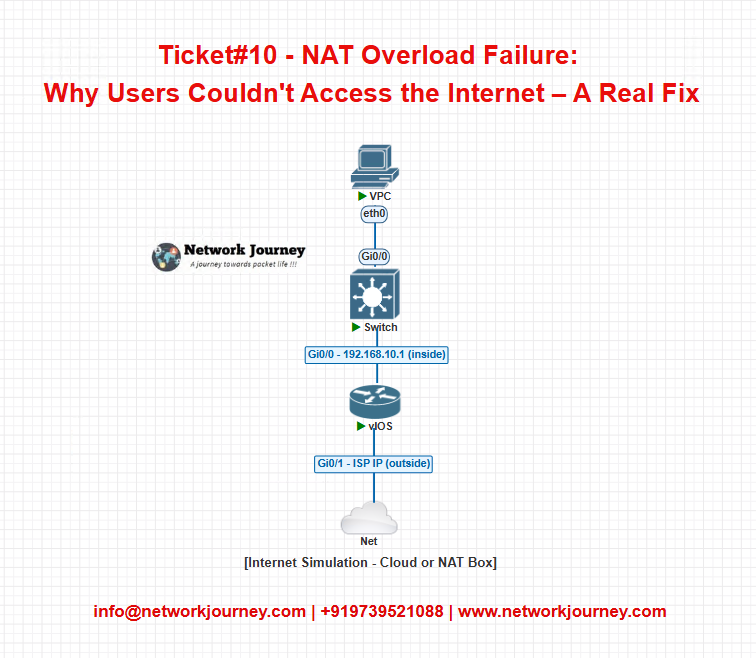
EVE-NG Devices:
- 1 Cisco vIOS-L2 (Access Layer)
- 1 Cisco vIOS-L3 (Core/Edge Router)
- 1 NAT Cloud Object
Verification
Run the following commands to verify NAT translations and ensure traffic is flowing:
show ip nat translations
show ip nat statistics
debug ip nat
Sample Output:
Pro Inside global Inside local Outside local Outside global
--- 203.0.113.5 192.168.10.10 8.8.8.8 8.8.8.8
- Users were then able to browse the internet
- Translation entries confirmed working NAT Overload
- Debug showed successful translations
Key Takeaways
- NAT Overload is crucial for private IP-to-public IP translation
- Missing
overloadkeyword = no PAT, no internet - Always match NAT ACLs with correct subnets
- Verification is easier with
show ip nat translations
Best Practice/Design Tips
- Always comment and document your NAT ACLs
- Automate NAT checks using Python/pyATS in production
- Don’t use a wide NAT ACL (e.g.,
any) — it can expose the network - Keep NAT stats and logs enabled for quick diagnosis
- Monitor NAT table size for scaling issues in enterprise environments
FAQs
1. Why is the overload keyword important in NAT?
Answer:
It enables Port Address Translation (PAT), allowing multiple private IPs to share a single public IP using different ports.
2. What happens if the NAT ACL doesn’t include a user subnet?
Answer:
That subnet won’t be translated, and traffic will fail as return packets can’t reach the source.
3. How do you check NAT configuration on a router?
Answer:
Use:
show run | section nat
show ip nat translations
4. Can incorrect NAT ACLs cause complete internet outage?
Answer:
Yes. If users are excluded from NAT translation, return traffic is dropped.
5. Why should I clear NAT translations?
Answer:
To remove stale or buggy sessions, especially after fixing or changing NAT rules.
6. How does NAT relate to internet access?
Answer:
It translates private IPs to public IPs, required for outbound communication to the public internet.
7. Can NAT overload be used on multiple interfaces?
Answer:
Yes, but each needs a separate ip nat outside definition and interface mapping.
8. What’s the difference between static NAT and NAT overload?
Answer:
- Static NAT maps one-to-one (1:1)
- NAT Overload maps many-to-one using ports (PAT)
9. What tool can simulate this scenario in labs?
Answer:
Use EVE-NG with Cisco IOSv images and NAT Cloud object or VirtualBox NAT adapter.
10. What if NAT is working, but DNS is not?
Answer:
Check if DNS packets are being NAT’d correctly or blocked by firewall/ACLs.
11. How do you monitor NAT performance?
Answer:
Use:
show ip nat statistics
Also monitor CPU/memory as high loads may affect translation.
12. Is NAT required in IPv6?
Answer:
No. IPv6 offers end-to-end reachability, making NAT unnecessary in most cases.
13. What if NAT translations are working but still no internet?
Answer:
Check default route, firewall, DNS issues, or possible asymmetric routing.
14. Can NAT be disabled temporarily for testing?
Answer:
Yes. Remove ip nat inside and ip nat outside from interfaces, but do this in test environments only.
15. How can I automate NAT troubleshooting?
Answer:
Use pyATS + Genie to run checks like:
pyats parse "show ip nat translations"
YouTube Link
Watch the Complete CCNP Enterprise: NAT Overload Failure: Why Users Couldn’t Access the Internet – A Real Fix Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement NAT Overload Failure: Why Users Couldn’t Access the Internet – A Real Fix is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Ticket#10 - NAT Overload Failure: Why Users Couldn't Access the Internet – A Real Fix [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-10.jpg)
![[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control](https://networkjourney.com/wp-content/uploads/2025/08/Day-42-Cisco-ISE-Mastery-Training-Integrating-Cisco-WLC-for-Wireless-Access-Control.png)
![[DAY#1 PyATS Series] What Is PyATS & Genie? Why Vendor‑Agnostic Testing? (Ping Tests) Using pyATS (Cisco/Arista/Paloalto/Fortigate) [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/07/DAY1-PyATS-Series-What-Is-pyATS_Genie-Why-Vendor‑Agnostic-Testing-Ping-TestsPython-for-Network-Engineernetworkjourney.png)
