Ticket#23: SSL VPN Users Cannot Reach Internal Resources – Split Tunnel ACL Error Fixed [CCNP Enterprise]
Table of Contents
Problem Summary
Users working remotely via Cisco AnyConnect VPN reported that while the VPN connection establishes successfully, they are unable to access any internal servers, applications, or file shares (e.g., 10.10.0.0/16 or 192.168.1.0/24).
- VPN tunnel status: Connected
- DNS resolution: Working
- Ping/SSH/RDP to internal IPs: Failed
- Affected: All users using split-tunneling profile
Symptoms Observed
- Users get an IP from the VPN pool (e.g., 172.16.100.0/24)
- Cannot access internal servers (e.g., 192.168.1.10)
- DNS resolves internal FQDNs correctly but no traffic returns
- No packet hits in ASA logs for internal access
- Split tunnel config is enabled, but traffic doesn’t route internally
Root Cause Analysis
Upon investigating the ASA config and using packet-tracer, the issue was narrowed down to a misconfigured split-tunnel ACL. The ACL defining “what to tunnel” did not include the internal subnets, so traffic to them was never sent over the tunnel in the first place.
Problematic ACL:
access-list SPLIT_TUNNEL standard permit 8.8.8.8
That ACL only permitted Google DNS — none of the internal networks were included, so the ASA was never told to tunnel that traffic.
Root Cause: Incomplete or incorrect split-tunnel ACL caused internal destinations to be bypassed, leading to connectivity failure.
The Fix
Step-by-Step Resolution:
- Check the Existing Split Tunnel ACL
show run access-list SPLIT_TUNNEL - Update the ACL with Internal Subnets
access-list SPLIT_TUNNEL standard permit 192.168.1.0 255.255.255.0 access-list SPLIT_TUNNEL standard permit 10.10.0.0 255.255.0.0 - Apply ACL to the VPN Group Policy
group-policy ANYCONNECT_POLICY attributes split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT_TUNNEL - Verify Group Policy Mapping
tunnel-group SSL-VPN-TUNNEL general-attributes default-group-policy ANYCONNECT_POLICY - Reconnect VPN and Retest
- Disconnect and reconnect the AnyConnect client
- Attempt to reach internal servers
EVE-NG Lab Topology
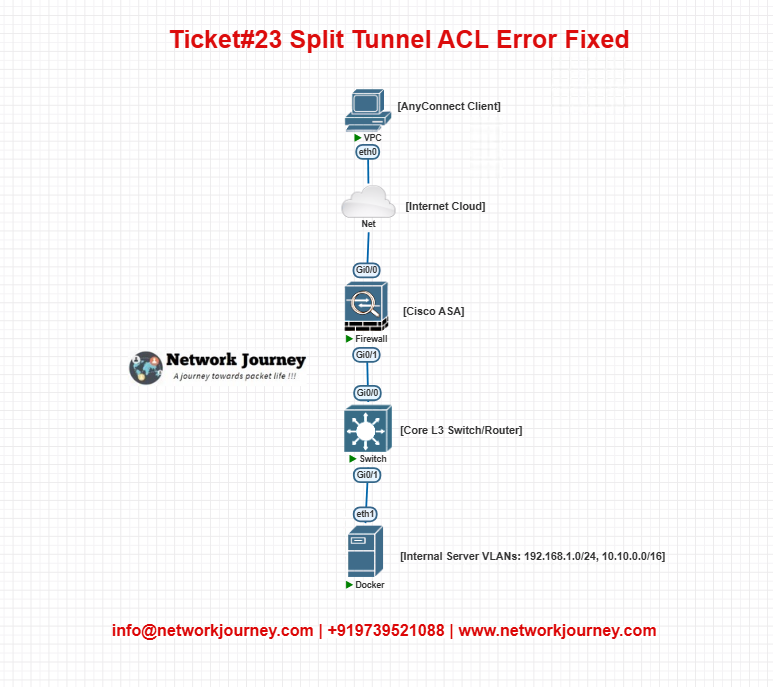
- Configure ASA with AnyConnect VPN
- Use split tunnel and simulate internal access
- Use internal pings or Wireshark for packet trace
Verification (Detailed)
CLI Verification
show vpn-sessiondb anyconnect show run group-policy | section split show access-list SPLIT_TUNNEL packet-tracer input outside tcp 172.16.100.10 12345 192.168.1.10 80
Expected Outcome:
- VPN tunnel up
- Split-tunnel ACL shows correct internal routes
- Packet tracer shows “allow” and next-hop correctly
- Users can ping and access internal apps
Key Takeaways
- Always double-check your split-tunnel ACL — it defines what traffic goes into the VPN
- Use
packet-tracerandshow vpn-sessiondbto debug routing issues - DNS resolution working doesn’t mean routing is correct
- Split-tunneling saves bandwidth but can silently drop routes if ACLs are incomplete
- Internal traffic must be explicitly defined in split-tunnel ACLs
Best Practice / Design Tips
- Use named ACLs and document them clearly
- Audit ACL entries regularly in your VPN config
- Always include all internal subnets used by clients in split-tunnel ACL
- Use DNS-based split tunneling (FQDN support) if available
- Prefer SNMP monitoring of session hits and access logs
- Migrate to SNMPv3 and enable syslog for VPN logs
- Test every new VPN policy with a clean user profile
- Define fallback group-policy for default failover
- Use hostnames or descriptions in ACLs for readability
- Monitor ASA CPU/memory during mass VPN usage
FAQs
1. Why does split-tunnel VPN sometimes fail to reach internal subnets?
Answer: The split-tunnel ACL may be missing or incorrectly defined. It controls what traffic is encrypted and sent through the tunnel.
2. Can DNS still resolve internal resources if split-tunnel ACL is wrong?
Answer: Yes. If DNS is tunneled or resolved via internal DNS, it can still respond, but actual traffic to the IP may fail without proper ACL inclusion.
3. How to check if traffic is being tunneled?
Answer: Use ipconfig /all on the client to view the assigned route or use netstat -rn. You can also run Wireshark on the client to confirm the traffic path.
4. What’s the command to view current VPN sessions?
show vpn-sessiondb anyconnect
5. Can I use FQDN instead of IPs in split-tunnel ACL?
Answer: Yes, Cisco ASA now supports FQDN-based ACLs in newer software versions for split tunneling.
6. What is the default split-tunnel behavior if not configured?
Answer: All traffic is tunneled through the VPN (full-tunnel mode).
7. Is it safe to use full-tunnel VPN instead of split-tunnel?
Answer: Full-tunnel is more secure but uses more bandwidth. Use it when strict security is required.
8. How to debug traffic from a VPN client to an internal server?
Answer: Use:
packet-tracer input outside <protocol> <client-ip> <port> <dest-ip> <dest-port>
9. Can split-tunnel ACL block access to Internet sites?
Answer: No. It only defines what traffic should be sent inside the tunnel. Internet traffic goes outside.
10. What logging level shows VPN ACL drops?
Answer: Level 6 (informational) and above. You can use:
debug vpn 255 debug webvpn 255
11. What version of ASA is needed for AnyConnect split-tunnel ACLs?
Answer: ASA 8.4 and above support split-tunnel ACLs; FQDN-based ACLs need newer versions (9.5+).
12. Can I apply different ACLs to different VPN groups?
Answer: Yes. Each group-policy can have its own split-tunnel-network-list.
13. Can I push routes to VPN clients dynamically?
Answer: Not via split-tunnel ACL, but you can configure ip local pool and group-policy with static routes.
14. Do split-tunnel ACLs apply to IKEv2/IPsec VPNs too?
Answer: Yes, though the configuration differs slightly between AnyConnect SSL and IPsec-based VPNs.
15. Can I simulate VPN behavior in EVE-NG?
Answer: Yes! Use a Windows VM with AnyConnect client and a Cisco ASA appliance with VPN setup to replicate the flow.
YouTube Link
Watch the Complete CCNP Enterprise: SSL VPN Users Cannot Reach Internal Resources – Split Tunnel ACL Error Fixed Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement SSL VPN Users Cannot Reach Internal Resources – Split Tunnel ACL Error Fixed is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Ticket#23: SSL VPN Users Cannot Reach Internal Resources – Split Tunnel ACL Error Fixed [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Ticket23-SSL-VPN-Users-Cannot-Reach-Internal-Resources-–-Split-Tunnel-ACL-Error-Fixed_networkjourney.png)
![[Day 38] – Cisco ISE Mastery Training: Wired Supplicant Configuration for Windows](https://networkjourney.com/wp-content/uploads/2025/08/Day-38-–-Cisco-ISE-Mastery-Training-Wired-Supplicant-Configuration-for-Windows.png)

![[Day 31] Cisco ISE Mastery Training: Wired Posture Assessment Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-31-–-Cisco-ISE-Mastery-Training-Wired-Posture-Assessment-Overview-1.png)