Ticket#6 – DHCP Not Working on Access Layer – Troubleshoot Snooping and Relay [CCNP ENTERPRISE]
Table of Contents
Problem Summary
In a mid-sized enterprise campus network, multiple users reported they were unable to get IP addresses from the DHCP server. The issue was isolated to specific access switches connected to VLAN 30. The DHCP server was reachable via Layer 3 on a core device, and other VLANs were not affected.
Symptoms Observed
- Devices on VLAN 30 showed 169.254.x.x (APIPA) addresses.
ipconfig /renewfailed on end-user machines.show ip dhcp bindinghad no recent entries.- Other VLANs on the same switch worked fine.
- Static IP assignment allowed communication.
Root Cause Analysis
Upon deeper investigation, the following issues were identified:
- DHCP Snooping was enabled, but the uplink interface was not marked as a trusted port.
- IP helper-address was missing on the interface VLAN for VLAN 30.
- Relay agent information option (Option 82) was dropping packets on upstream devices.
These caused DHCP Discover messages to be dropped or never reach the DHCP server.
The Fix
Steps Taken to Fix the Issue:
- Marked the uplink trunk port as trusted:
interface GigabitEthernet1/0/24 ip dhcp snooping trust - Verified VLAN configuration and SVI status:
interface vlan 30 ip address 10.30.0.1 255.255.255.0 ip helper-address 10.10.10.100 - Verified DHCP Snooping configuration:
ip dhcp snooping ip dhcp snooping vlan 30 - Ensured no conflicts with Option 82 if not used:
no ip dhcp snooping information option - Saved the configuration and rebooted one client to verify DHCP lease.
EVE-NG Lab Topology
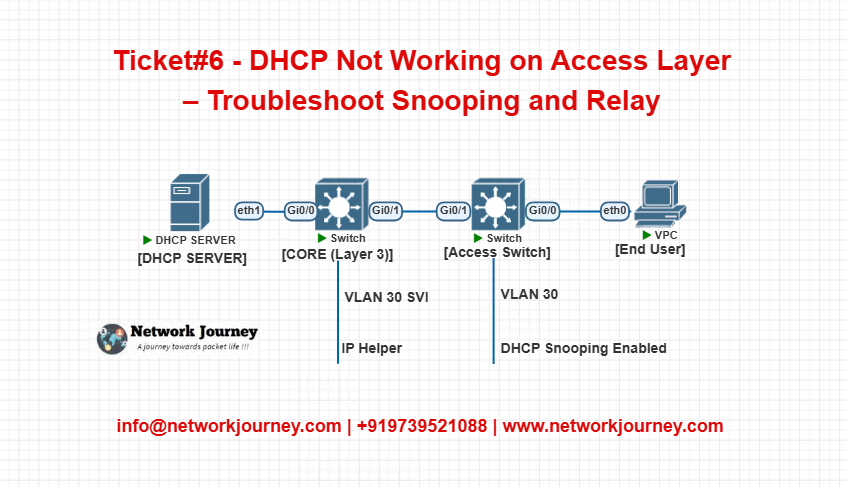
Device Configs :
Core Switch:
interface Vlan30
ip address 10.30.0.1 255.255.255.0
ip helper-address 10.10.10.100
Access Switch:
ip dhcp snooping
ip dhcp snooping vlan 30
interface Gig1/0/24
description Uplink to Core
switchport mode trunk
ip dhcp snooping trust
interface Gig1/0/1
description End Device
switchport mode access
switchport access vlan 30
Verification
| Command | Purpose |
|---|---|
show ip dhcp snooping | Verify DHCP snooping is enabled |
show ip dhcp snooping binding | View learned bindings |
debug ip dhcp server packet | Analyze DHCP packet flow |
ping <gateway> | Verify gateway reachability |
ipconfig /renew (PC) | Test DHCP lease renewal |
Key Takeaways
- Always trust uplink ports when DHCP Snooping is enabled.
- Don’t forget to configure IP helper-address on SVIs.
- Disable Option 82 insertion unless it’s used/understood.
- Check if VLAN is correctly allowed on trunks.
- Use debugs and packet captures to trace packet flow.
Best Practices/Design Tips
- Keep DHCP server in a secure central VLAN, reachable via L3.
- Enable DHCP snooping on access switches only.
- Avoid enabling snooping on uplinks unless trusted.
- Periodically clear bindings if testing in lab environments.
- Consider logging DHCP drops using
ip dhcp snooping logging.
FAQs with Answers
1. Why is DHCP Snooping required in enterprise networks?
Answer:
DHCP snooping prevents rogue DHCP servers from offering IP addresses to users, which can lead to traffic interception or DoS attacks.
2. What happens if a port is not trusted under DHCP Snooping?
Answer:
DHCP Offer/Ack packets received on untrusted ports are dropped, preventing clients from receiving IP addresses.
3. What is the purpose of the IP helper-address command?
Answer:
It allows a router or Layer 3 switch to forward DHCP broadcast packets to a unicast DHCP server in another network.
4. Can I use DHCP Snooping without IP helper-address?
Answer:
Only if the DHCP server is in the same VLAN. If it is in another VLAN, ip helper-address is essential.
5. What is Option 82, and why does it cause issues?
Answer:
Option 82 adds metadata about where the DHCP request originated. If not supported or mismatched, the DHCP server may reject the request.
6. How to identify if DHCP snooping is dropping packets?
Answer:
Use:
show ip dhcp snooping
show ip dhcp snooping statistics
Look for drop counts or errors.
7. Does DHCP Snooping work across trunks?
Answer:
Yes, but ensure the trunk port is trusted, and VLANs are allowed on the trunk.
8. What is the default lease time in DHCP?
Answer:
It depends on the server config, but usually 24 hours (86400 seconds) unless specified.
9. How can I simulate DHCP issues in EVE-NG?
Answer:
- Remove helper-address.
- Disable snooping trust.
- Block trunk VLANs.
- Capture packets using Wireshark in the topology.
10. What’s the best way to test DHCP after config changes?
Answer:
- Clear existing leases.
- Use
ipconfig /releaseand/renew. - Use
debug ip dhcp server packetor capture traffic.
11. Should I enable DHCP Snooping globally?
Answer:
Yes, with the command ip dhcp snooping, and then specify VLANs with ip dhcp snooping vlan X.
12. What’s the difference between a trusted and untrusted port in DHCP Snooping?
Answer:
- Trusted: DHCP responses allowed (e.g., uplinks)
- Untrusted: Only DHCP requests allowed (e.g., host ports)
13. What happens if multiple DHCP servers exist in the same VLAN?
Answer:
Clients may get IPs from unintended DHCP servers. Snooping ensures only trusted servers respond.
14. Can DHCP Snooping block static IPs?
Answer:
No. DHCP snooping only tracks dynamic assignments. Static IPs will bypass the binding table.
15. What else works with DHCP Snooping?
Answer:
- DAI (Dynamic ARP Inspection)
- IP Source Guard
Both depend on DHCP Snooping binding tables.
YouTube Link
Watch the Complete CCNP Enterprise: DHCP Not Working on Access Layer – Troubleshoot Snooping and Relay Demo & Explanation on our channel:
Class 4 Traditional Network Topology vs SD Access Simplified
Final Note
Understanding how to differentiate and implement DHCP Not Working on Access Layer – Troubleshoot Snooping and Relay is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Ticket#6 - DHCP Not Working on Access Layer – Troubleshoot Snooping and Relay [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-6.jpg)
![Still Using SNMPv2? Here’s Why You Must Switch to SNMPv3 Today! [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-snmpv3.jpg)
![Model-Driven Telemetry vs SNMP – Rethinking Network Monitoring [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Model-Driven-Telemetry-vs-SNMP-–-Rethinking-Network-Monitoring-1.png)
![Mastering Syslog Levels and Configuration in Cisco Networks [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-Syslog-Levels-and-Configuration-in-Cisco-Networks_networkjourney.png)