Ticket#3 – VLAN Mismatch: End Users Unable to Reach Gateway – A Real Cisco Fix [CCNP ENTERPRISE]
Table of Contents
Problem Summary
Multiple end-users on the 3rd floor raised a complaint that they were unable to reach the default gateway. They couldn’t access internal resources or the internet. The issue was isolated to a single switch block, while other floors remained unaffected.
The NOC team initially suspected DHCP or routing issues, but the problem turned out to be a classic VLAN mismatch—a silent killer in Layer 2 environments.
Symptoms Observed
- Users couldn’t ping the gateway (e.g.,
192.168.10.1) - No DHCP address received; APIPA (
169.x.x.x) was assigned show cdp neighborsrevealed correct uplink to the distribution switch- The trunk was up/up, but no MACs learned on user ports
- Other floors using the same VLAN ID were unaffected
Root Cause Analysis
After Layer 1/2 checks, the following was found:
- Access switch ports were assigned to VLAN 10 (user VLAN)
- But the uplink trunk to distribution switch did not allow VLAN 10
- On the distribution switch, VLAN 10 was mapped to a different subnet
- There was a mismatch in VLAN configuration, i.e.,
- VLAN 10 on Access Switch ≠ VLAN 10 on Distribution Switch
In short, same VLAN ID but different purpose, resulting in broken L2 forwarding.
The Fix
- Verify VLAN Status
- Used
show vlan briefandshow interfaces trunkon both switches
- Used
- Validate Allowed VLANs
- Confirmed
VLAN 10was not in theallowed vlan liston the trunk port
- Confirmed
- Match VLAN Naming Convention
- Found VLAN 10 was named “Voice” on the distribution switch
while access switch used it for “Users”
- Found VLAN 10 was named “Voice” on the distribution switch
- Reconfigure VLAN and Trunk
- Changed user ports to correct VLAN (VLAN 20)
- Updated trunk ports to carry correct VLANs across the link
- Add Missing VLAN if Needed
- Created VLAN on upstream switch:
vlan 20→name Users
- Created VLAN on upstream switch:
EVE-NG Lab Topology
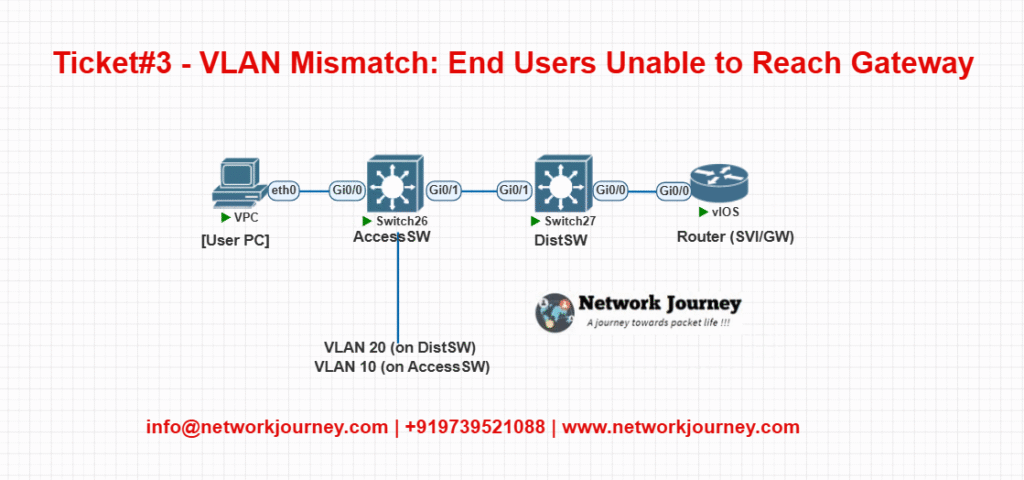
CLI Fix Simulation
Access Switch:
interface range fa0/1 - 24
switchport mode access
switchport access vlan 20
Trunk Check:
show interfaces trunk
Trunk Allow Fix:
interface gi0/1
switchport trunk allowed vlan add 20
Create VLAN:
vlan 20
name Users
Verify:
show vlan brief
show mac address-table
Verification
| Step | Command | Expected Output |
|---|---|---|
| VLAN existence check | show vlan brief | VLAN 20 listed on both switches |
| Trunk port status | show interfaces trunk | VLAN 20 allowed |
| Ping from user PC | ping 192.168.20.1 | Successful |
| MAC learning check | show mac address-table | MACs learned in VLAN 20 |
| DHCP allocation | show ip dhcp binding | IPs assigned from correct subnet |
Key Takeaways
- VLAN mismatch is often a silent issue with no interface errors.
- Trunk ports must carry all necessary VLANs.
- Never assume same VLAN ID means same purpose — always use naming conventions.
- Check both access and distribution layers for alignment.
- VLANs not being passed = broken L2 domain = no gateway reachability.
Best Practices & Design Tips
- Always use unique VLAN IDs per function (Data, Voice, etc.)
- Apply naming conventions to VLANs (
Users,Voice,Server) to avoid confusion - Enable VTP in transparent mode or use VLAN databases carefully
- Use port-based VLAN monitoring tools (NetFlow, SPAN)
- Regularly audit trunk port configurations
FAQs – VLAN Mismatch Troubleshooting
1. What is a VLAN mismatch?
Answer:
It occurs when two ends of a trunk or port carry different VLANs or VLANs with the same ID but different purposes, breaking Layer 2 forwarding.
2. Why didn’t CDP or port status indicate any issue?
Answer:
Because physical link and trunking (802.1Q) was operational, but Layer 2 was misaligned, so no errors were generated.
3. Can same VLAN ID be used for different functions?
Answer:
Yes, but it’s not recommended. Use consistent ID and name conventions across the network.
4. How do I know if a VLAN is missing on a switch?
Answer:
Use:
show vlan brief
If the VLAN isn’t listed, it’s missing.
5. What happens if a VLAN is not allowed on a trunk?
Answer:
Traffic for that VLAN is not forwarded between switches, causing end-users to lose access to upstream resources.
6. How do I allow a VLAN on a trunk?
Answer:
interface gi0/1
switchport trunk allowed vlan add 20
7. Will mismatched native VLAN cause this issue?
Answer:
Not exactly. Native VLAN mismatches cause CDP warnings and potential tagging issues, but not silent breakage like this.
8. Why did users get APIPA addresses?
Answer:
Because DHCP packets could not reach the server due to the VLAN isolation, so clients self-assigned 169.x.x.x.
9. How to prevent VLAN mismatches in future?
Answer:
- Document VLAN ID vs purpose
- Use consistent VLAN names
- Run regular audits with
show interfaces trunk
10. Should I use VTP to avoid such issues?
Answer:
Not necessarily. VTP has its own risks (VTP bombs). Better to manually manage VLANs or use automation tools.
11. Can this issue affect VOIP phones?
Answer:
Yes. If voice VLANs are misaligned or not passed, phones won’t register with call manager.
12. Is this common in new switch deployments?
Answer:
Yes. It often happens when switches are cloned, copied, or not properly documented.
YouTube Video
Final Note
Understanding how to differentiate and implement VLAN Mismatch: End Users Unable to Reach Gateway – A Real Cisco Fix is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Ticket#3 - VLAN Mismatch: End Users Unable to Reach Gateway – A Real Cisco Fix [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket3.jpg)

![Route Redistribution with Tagging – Mastering Controlled Routing Across Protocols [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/Route-Redistribution-with-Tagging-–-Mastering-Controlled-Routing-Across-Protocols-CCNP-ENTERPRISE-.png)
![Introduction to JSON & YANG – The Foundation of Network Automation [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Introduction-to-JSON_YANG–The-Foundation-of-Network-Automation_networkjourney.png)