AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide [CCNP ENTERPRISE]
Let me take you back to my early network engineering days. We had 10 routers and 20 engineers—and we used the same username and password across all devices. No logs. No traceability. Just convenience… until one fine day, someone made a change that brought the network down—and we had zero visibility into who did it.
That day, I realized that security and accountability in network access isn’t optional—it’s essential.
That’s where AAA (Authentication, Authorization, and Accounting) with RADIUS and TACACS+ comes in.
If you’re preparing for CCNA/CCNP or managing an enterprise network, this article will be your go-to guide to implement AAA with CLI examples, real use cases, and an EVE-NG lab to tie it all together.
Table of Contents
Theory in Brief
What is AAA?
AAA stands for Authentication, Authorization, and Accounting, and it’s the framework for managing who can access a network device, what they can do, and tracking every action.
- Authentication: Who are you? (Username/Password check)
- Authorization: What are you allowed to do?
- Accounting: What did you do, and when?
What are RADIUS and TACACS+?
AAA uses backend servers to process credentials. Two protocols dominate:
- RADIUS (Remote Authentication Dial-In User Service):
- Combines authentication and authorization
- Uses UDP (port 1812)
- Encrypts only passwords
- Mostly used for network access (Wi-Fi, VPN, etc.)
- TACACS+ (Terminal Access Controller Access-Control System Plus):
- Separates authentication and authorization
- Uses TCP (port 49)
- Encrypts entire payload
- Commonly used for device admin access
Local vs Server-Based AAA
You can configure local AAA with usernames stored in the router/switch, or you can point the device to a TACACS+/RADIUS server like Cisco ISE, FreeRADIUS, or TACACS.net.
Server-based AAA is scalable, auditable, and secure—perfect for production environments.
Why Use AAA?
- Role-based access control
- Log every change made via CLI
- Block/allow users from a central server
- Compliance (PCI-DSS, ISO, etc.)
If your network matters, AAA matters.
AAA: RADIUS vs TACACS+ Comparison
| Feature | RADIUS | TACACS+ |
|---|---|---|
| Transport Protocol | UDP | TCP |
| Port | 1812 (Auth), 1813 (Acct) | 49 |
| Encryption | Password Only | Full Payload |
| Authentication/Authz | Combined | Separate |
| Use Case | Access (VPN, Wi-Fi) | Admin Login (SSH, Console, Telnet) |
| Cisco Recommended | Yes (For Network Access) | Yes (For Device Admin Access) |
Summary
| Task | CLI Command Example | Description |
|---|---|---|
| Enable AAA | aaa new-model | Turns on AAA framework |
| Define TACACS+ server | tacacs-server host 10.1.1.100 key Network@123 | Add TACACS+ server details |
| Define RADIUS server | radius-server host 10.1.1.101 key Radius@123 | Add RADIUS server details |
| Define method list | aaa authentication login default group tacacs+ local | Use TACACS+, fallback to local |
| Apply AAA on VTY lines | line vty 0 4login authentication default | Apply method list to remote access |
| View active users | show users | See who’s logged in |
| View AAA config | `show run | include aaa` |
| Debug AAA | debug aaa authentication, debug tacacs, debug radius | Real-time troubleshooting |
Use Case
| Scenario | Problem | AAA Benefit |
|---|---|---|
| ISP with 50+ routers | No central login control, passwords everywhere | Centralize login with TACACS+ |
| Financial institution | Needs audit logs of CLI commands | Use TACACS+ with accounting |
| Wi-Fi Access via Captive Portal | Users connect without tracking | Use RADIUS for 802.1X authentication |
| Multi-admin environment | Everyone uses shared credentials | AAA assigns unique users with per-user access |
Lab: TACACS+ Configuration (With Realistic Testing)
TOPOLOGY OVERVIEW
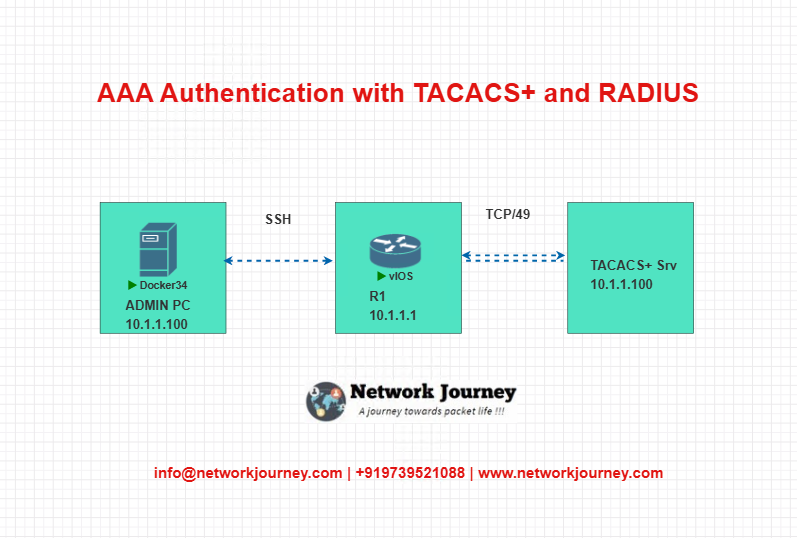
Step-by-Step Lab Configuration
Step 1: Enable AAA
aaa new-model
Step 2: Configure TACACS+ Server
tacacs-server host 10.1.1.100 key Network@123
Step 3: Define Authentication Method List
aaa authentication login default group tacacs+ local
Step 4: Apply AAA to VTY Lines
line vty 0 4
login authentication default
Step 5: Optional Local Fallback User
username admin secret fallback@123
Testing Scenarios
| Test Case | Expected Result |
|---|---|
| TACACS+ login from Admin PC | Successful if user is valid |
| Invalid TACACS+ user login | Access Denied |
| TACACS+ server offline + local user | Fallback login allowed |
Troubleshooting Tips
| Symptom | Possible Cause | Fix |
|---|---|---|
| Login always fails | Wrong key or server IP | Recheck tacacs-server host config |
| Login times out | UDP packet drop (RADIUS) or port issue | Check firewall, verify UDP/1812 or TCP/49 |
| Local fallback not working | Not defined or wrong method list | Add local to end of method list |
| Debug not showing results | Debug not enabled or logging turned off | Run debug aaa authentication, term mon |
| Wrong method list used | Misapplied under VTY or not named properly | Apply with login authentication <list> |
FAQs
What is the primary purpose of implementing AAA in a network?
Answer:
AAA helps secure access to network devices by:
- Authentication: Verifying user identity before allowing access
- Authorization: Granting specific permissions based on user roles
- Accounting: Logging actions performed by users for auditing purposes
This framework ensures only authorized users gain access and their activities are traceable.
2: How does RADIUS differ from TACACS+ in terms of functionality?
Answer:
Here’s a comparison between the two:
- RADIUS:
- Uses UDP (faster, less reliable)
- Combines authentication and authorization
- Encrypts only the password
- Suitable for Wi-Fi, VPN, and user access
- TACACS+:
- Uses TCP (connection-oriented)
- Separates authentication, authorization, and accounting
- Encrypts the entire payload
- Preferred for device administration and command-level control
3: Can I use both RADIUS and TACACS+ in a single network?
Answer:
Yes, you can. Many organizations use:
- TACACS+ for network device (router/switch) administrative access
- RADIUS for user authentication on VPN, Wi-Fi, and 802.1X setups
You can define separate AAA method lists for different services.
4: What happens if the AAA server goes down?
Answer:
If the AAA server becomes unreachable, the device will:
- Check the method list applied to the login method (VTY, Console, etc.)
- If the list includes a fallback (e.g.,
local), it will use local credentials - If no fallback is configured, access will be denied
Best Practice: Always include local at the end of the method list for redundancy.
5: Is TACACS+ a Cisco proprietary protocol?
Answer:
Yes, TACACS+ is Cisco proprietary, but it is widely supported by:
- Third-party devices like Fortinet, Palo Alto, and Juniper
- Open-source tools like tacacs.net, FreeTACACS+, and commercial systems like Cisco ISE
6: What is the best way to test AAA authentication in a lab?
Answer:
Follow these steps in an EVE-NG or GNS3 lab:
- Set up a Cisco router or switch with
aaa new-model - Configure a TACACS+ or RADIUS server VM (tacacs.net or FreeRADIUS)
- Create a user on the server
- Try logging into the router via SSH
- Observe whether access is granted or denied and check logs/debugs
Use debug aaa authentication and debug tacacs or debug radius for real-time output.
7: Can I log every command a user runs using AAA?
Answer:
Yes, especially with TACACS+, which supports command accounting.
You can:
- Log each EXEC and configuration command
- Track time, user, device, and command history centrally
- Use Cisco ISE, ACS, or other TACACS+ servers with accounting enabled
This helps in compliance and forensic audits.
8: How can I integrate Windows Server with RADIUS?
Answer:
You can use NPS (Network Policy Server), which is Microsoft’s implementation of RADIUS.
Steps:
- Install NPS role on Windows Server
- Register the server in Active Directory
- Add the router/switch as a RADIUS client
- Create a connection request and network policy
- Define shared secrets and test login
NPS integrates with AD to use domain credentials.
9: What are the default ports used by TACACS+ and RADIUS?
Answer:
- TACACS+: TCP port 49
- RADIUS:
- UDP port 1812 for Authentication
- UDP port 1813 for Accounting
Make sure these ports are open on your firewalls between the device and the AAA server.
10: What are some common AAA misconfigurations to avoid?
Answer:
Some common issues include:
- Forgetting to add a local fallback in method lists
- Misconfiguring server IP or shared secret
- Not applying AAA to VTY or console lines
- Using default method list when a named list is required
- Incorrect debug usage (not enabling
term monwhile troubleshooting)
Tip: Always verify with show run | include aaa and test before deploying in production.
YouTube Link
Watch the Complete CCNP Enterprise: AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-AAA-TACACS-RADIUS.jpg)
![Mastering Layer 2 Troubleshooting Commands: A Complete Guide with CLI & EVE-NG Labs [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-Layer-2-Troubleshooting-Commands_networkjourney.png)

![[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control](https://networkjourney.com/wp-content/uploads/2025/08/Day-42-Cisco-ISE-Mastery-Training-Integrating-Cisco-WLC-for-Wireless-Access-Control.png)