[Day 142 ] Cisco ISE Mastery Training: External RADIUS Proxy for Cloud NAC
Table of Contents
Introduction
In modern enterprise networks, security no longer ends at the perimeter. As organizations adopt cloud-based NAC, BYOD, and multi-vendor wireless solutions, a challenge arises: how do you centralize authentication, authorization, and auditing without duplicating identity stores or exposing internal RADIUS infrastructure directly to the internet?
The answer: External RADIUS Proxy. Cisco ISE acts as a policy decision point, while an external RADIUS proxy can forward authentication requests to cloud-based NAC services (or multiple ISE nodes) while preserving security, scalability, and compliance.
In this Article, l will not only configure the external RADIUS proxy, but also validate authentication flows, troubleshoot failures, and implement real-world use cases. By the end, you will be able to design and deploy a hybrid NAC architecture that integrates seamlessly with both on-prem and cloud infrastructure.
Problem Statement
Real-world challenges solved by external RADIUS proxy:
- Multi-domain authentication: Enterprise networks often have multiple ISE instances or external NAC systems. Centralizing authentication requests avoids misconfigurations.
- Cloud NAC integration: Directly exposing internal RADIUS servers to cloud endpoints is risky. A proxy provides a secure relay.
- Scalability & redundancy: Multiple proxies allow failover and load balancing for high availability.
- Policy consistency: Ensures that authorization policies are applied uniformly across all access points, wired/wireless, and cloud endpoints.
- Simplified auditing: Centralized logging via ISE ensures compliance without managing multiple endpoints independently.
Solution Overview
Cisco ISE supports RADIUS proxy functionality where it acts as an intermediary:
- Receives RADIUS requests from network devices (switches, WLCs, VPN).
- Forwards requests to the appropriate target server (cloud NAC, another ISE, or third-party RADIUS).
- Maintains attribute integrity, supports multiple authentication methods, and allows per-request routing based on policies (source IP, NAS ID, user attributes).
- Provides GUI & CLI tools for monitoring and validation, including Live Logs, Authentication Reports, and debugging commands.
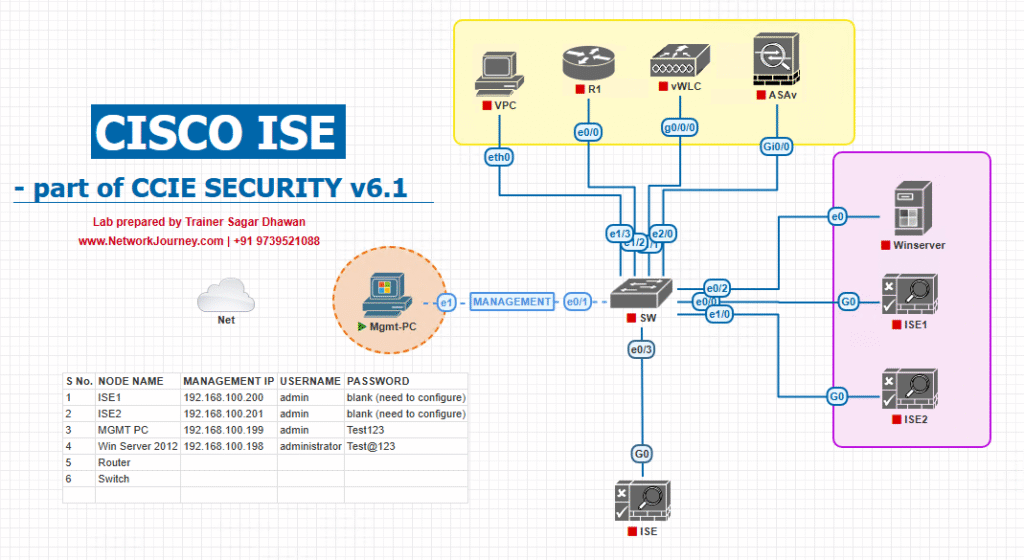
Sample Lab Topology
Topology for VMware/EVE-NG Lab:
| Device | IP Address | Role |
|---|---|---|
| ISE Primary Node (VM) | 10.50.1.10 | RADIUS proxy configuration |
| ISE Secondary Node | 10.50.1.11 | HA / backend authentication server |
| Cloud NAC (simulated) | 10.50.2.20 | RADIUS target |
| WLC (VM/Physical) | 10.50.1.20 | Wi-Fi Controller, forwards 802.1X requests |
| Access Switch | 10.50.1.5 | 802.1X wired client |
| Endpoints | DHCP 10.50.1.x | Test clients for authentication |
| Admin Workstation | 10.50.1.100 | For GUI, CLI, Postman/curl testing |
Diagram:
Step‑by‑Step GUI Configuration Guide
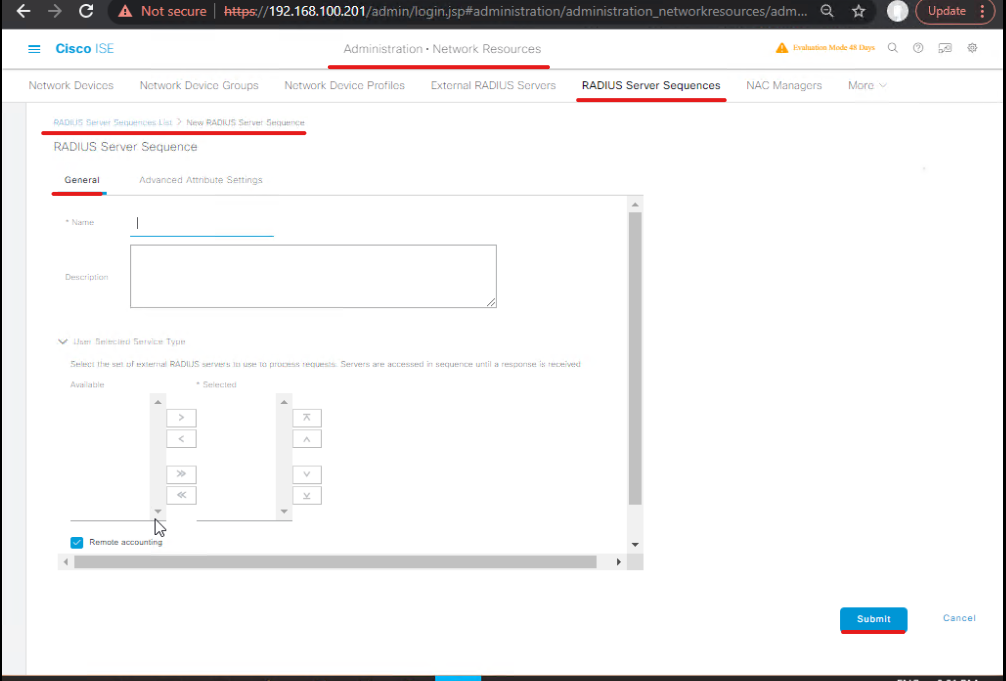
A – Configure RADIUS Target for Cloud NAC
Step 1: Login to ISE Admin GUI → Administration → Network Resources → Network Devices / RADIUS Targets
Step 2: Click Add → RADIUS Server
- Name:
CloudNAC-Radius - IP Address:
10.50.2.20 - Authentication Port:
1812 - Accounting Port:
1813 - Shared Secret:
CloudSecret123 - Retry / Timeout:
3 retries, 5s timeout - Check Enabled
[Screenshot placeholder: ISE RADIUS Target Configuration Screen]
Step 3 – Validate RADIUS Target:
- GUI: Test Connection button
- CLI:
ping 10.50.2.20 show radius server group CloudNAC-Radius
- Expected Result: Ping successful, RADIUS server group displayed.
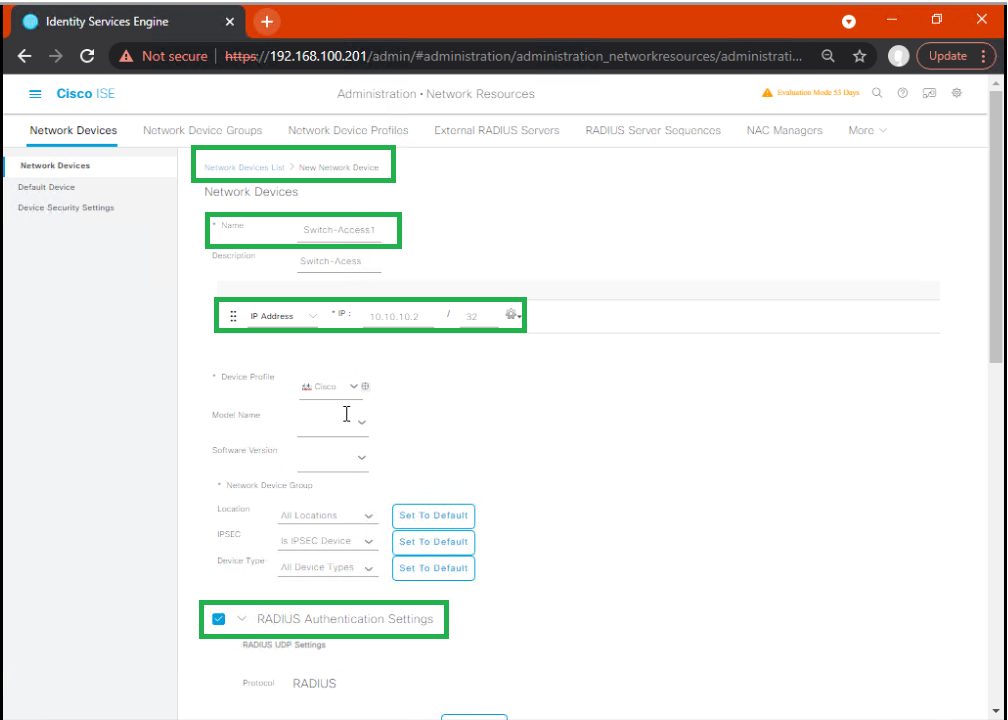
B – Configure Network Device (WLC / Switch) in ISE
Step 1: Administration → Network Resources → Network Devices → Add
- Name:
WLC-01 - IP Address:
10.50.1.20 - Device Type:
Wireless LAN Controller - Shared Secret:
WLCSecret123
[Screenshot placeholder: Network Device Add Screen]
Step 2 – Assign RADIUS Target:
- Under RADIUS Authentication: Select Proxy to CloudNAC-Radius
Step 3 – Validate:
- GUI: Operations → RADIUS Live Logs → Test Authentication
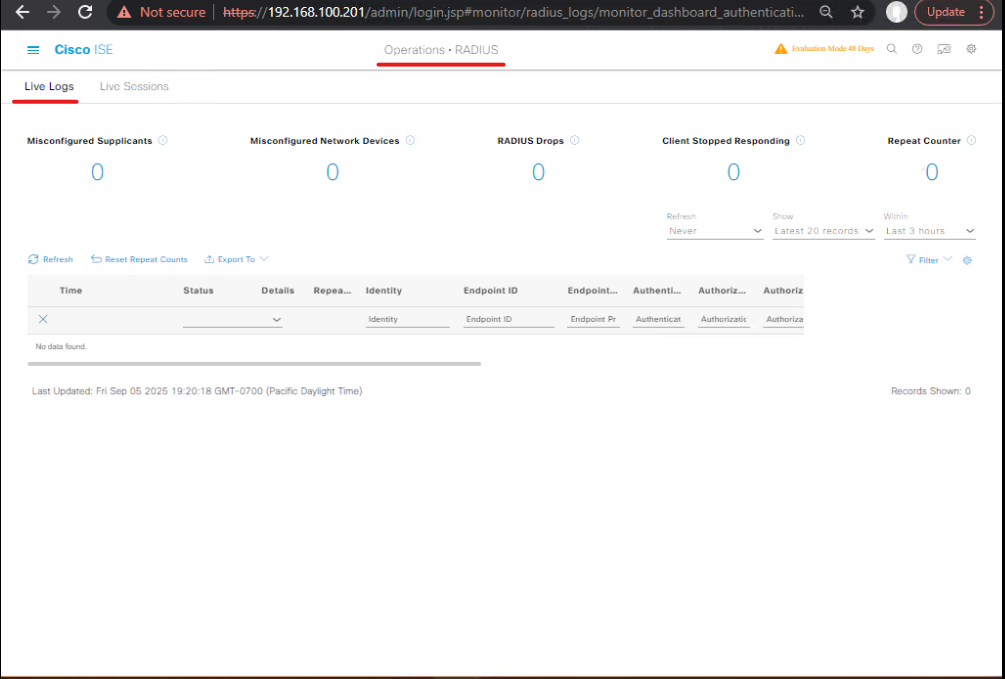
- CLI:
debug radius authentication show radius statistics
- Expected Result: Incoming request from NAS seen, forwarded to cloud NAC.
C – Configure Policy Set for RADIUS Proxy
Step 1: Policy → Policy Sets → Add New Policy Set
- Name:
Cloud NAC Proxy Policy - Condition:
NAS-IP = 10.50.1.20(WLC IP)
Step 2 – Authentication Policy:
- Select Use RADIUS Proxy
- Target:
CloudNAC-Radius
Step 3 – Authorization Policy:
- Map attributes returned by Cloud NAC → ISE Authorization Profile
- Example:
CloudNAC-Guest → Guest-VLAN-100
[Screenshot placeholder: Policy Set Authentication & Authorization Screen]
Step 4 – Validate:
- GUI: Connect test client → Operations → RADIUS Live Logs
- CLI:
show authentication sessions show radius statistics
- Expected Result: Proxy target correctly used, Access-Accept returned, correct VLAN/ACL applied.
D – Configure Backup / Failover RADIUS Target (Optional)
Step 1: Add secondary RADIUS Target → CloudNAC-Secondary
- IP Address:
10.50.2.21 - Ports, Secret, Retry/Timeout same as primary
Step 2: Add both targets to RADIUS Target Group
- Primary = CloudNAC-Radius, Secondary = CloudNAC-Secondary
Step 3 – Configure Policy Set
- Authentication → Use Target Group
- Ensure failover order is correct
Step 4 – Validate Failover:
- GUI: Disconnect primary NAC, authenticate test client → Operations → RADIUS Live Logs
- CLI:
debug radius authentication show radius statistics
- Expected Result: Requests forwarded to secondary, Access-Accept returned.
E – Test End-to-End Client Authentication
- Connect test laptop/mobile to Guest SSID.
- Observe redirect (if cloud NAC uses captive portal).
- Validate in GUI: Operations → RADIUS Live Logs
- Field:
Proxy Target = CloudNAC-Radius
- Field:
- CLI validation:
show authentication sessions debug radius authentication show radius statistics
- Confirm Authorization Profile applied correctly (VLAN, ACL, ACL download).
F – CLI Quick Reference Commands for Validation
| Purpose | CLI Command |
|---|---|
| View RADIUS server group | show radius server group |
| Ping RADIUS target | ping <IP> |
| Show authentication sessions | show authentication sessions |
| Debug authentication | debug radius authentication |
| Show RADIUS statistics | show radius statistics |
| Check running config for proxy | show running-config radius |
This section is full step-by-step GUI + CLI guide, includes:
- RADIUS target config
- Network device setup
- Policy set creation
- Failover / backup target setup
- End-to-end validation
- CLI quick commands for real-time troubleshooting
Troubleshooting & Diagnostics – External RADIUS Proxy for Cloud NAC
1. Verify Network Connectivity
Objective: Ensure that the ISE proxy can reach the cloud NAC RADIUS server.
Step-by-Step:
- Ping the Cloud NAC Target
ping 10.50.2.20- Expected Result: Successful ping → network reachable.
- Traceroute to verify path
traceroute 10.50.2.20- Validate there are no firewalls or NAT devices blocking RADIUS ports (1812/1813).
- GUI Check:
- ISE → Administration → Network Resources → RADIUS Targets → Test Connection
Common Issues:
- Firewall blocking UDP 1812/1813
- Incorrect IP address or DNS resolution failure
2. Validate RADIUS Target Configuration
Step-by-Step:
- Check RADIUS server group
show radius server group CloudNAC-Radius- Validate IP, ports, shared secret, retry/timeout.
- Check Target Enabled Status
- GUI: Administration → Network Resources → RADIUS Targets → Status column should show Enabled
Common Issues:
- Disabled target
- Mismatched shared secret → Access-Reject
3. Check Policy Set Mapping
Objective: Ensure authentication requests match the correct policy set.
Step-by-Step:
- GUI: Policy → Policy Sets → Verify conditions
- NAS IP / Device IP matches WLC/Switch
- Authentication policy → Forward to RADIUS Proxy
- CLI: Validate active sessions:
show authentication sessions- Check
Policy Set Name→ must match expected policy
- Check
Common Issues:
- NAS IP mismatch → request routed to default policy
- Incorrect conditions → fallback to internal authentication
4. Debug RADIUS Authentication
Objective: See live authentication traffic and proxy behavior.
Step-by-Step:
- Enable debug:
debug radius authentication - Initiate test authentication from endpoint
- Observe logs:
- Look for
Proxy Target = CloudNAC-Radius - Check Access-Accept / Access-Reject messages
- Look for
- GUI: Operations → RADIUS Live Logs
- Fields to verify:
NAS IP,User,Proxy Target,Authorization Profile
- Fields to verify:
Common Issues:
- Access-Reject from cloud NAC → check shared secret and authentication method
- No logs → check NAS forwarding configuration
5. Check Authorization Attributes
Objective: Ensure VLAN / ACL / role is applied correctly.
Step-by-Step:
- GUI: Operations → RADIUS Live Logs → Open authentication details
- Verify returned attributes:
Tunnel-Private-Group-ID→ VLAN assignmentFilter-Id→ ACL applied
- CLI:
show authentication sessions detail show radius statistics
Common Issues:
- Attribute mapping misconfigured in ISE → authorization profile not applied
- Cloud NAC not returning expected RADIUS attributes
6. Failover / Redundancy Troubleshooting
Objective: Ensure secondary RADIUS target is used if primary fails.
Step-by-Step:
- Simulate primary failure (shutdown primary cloud NAC or block RADIUS port)
- Authenticate test endpoint
- Validate logs:
- GUI: Live Logs →
Proxy Target = CloudNAC-Secondary - CLI:
debug radius authentication→ observe failover attempts
- GUI: Live Logs →
Common Issues:
- Retry / timeout misconfigured → requests drop instead of failover
- Secondary target not in proxy target group
7. Time / Certificate Validation (SAML / EAP-TLS scenarios)
Objective: Ensure proxy and NAC clocks and certificates are valid.
- CLI: Check NTP sync
show ntp status - GUI: Verify certificates for EAP-TLS / PEAP if using cloud NAC with certificate-based auth
- Test client authentication → validate certificate chain
Common Issues:
- Clock skew → authentication fails
- Untrusted certificates → Access-Reject
Advanced Diagnostics
Commands / Tools:
| Purpose | CLI / Tool |
|---|---|
| Display RADIUS server group details | show radius server group <name> |
| Live authentication sessions | show authentication sessions |
| Debug authentication traffic | debug radius authentication |
| Show RADIUS statistics | show radius statistics |
| Check running config | show running-config radius |
| Capture SAML / EAP-TLS attributes | Browser SAML-tracer / Wireshark on test endpoint |
| Test RADIUS reachability | nc -u <IP> 1812 or telnet <IP> 1812 |
Common Troubleshooting Scenarios
| Symptom | Possible Cause | Resolution |
|---|---|---|
| Access-Reject | Shared secret mismatch | Update secret on ISE and NAC |
| No RADIUS response | Network/firewall issue | Verify UDP 1812/1813, routing, NAT |
| Wrong Authorization Profile applied | Cloud NAC returned unexpected attributes | Update ISE policy mapping |
| Failover not working | Secondary target misconfigured | Add to target group, adjust retry/timeout |
| Client cannot connect | NAS not sending RADIUS requests to ISE | Verify NAS IP & shared secret |
Best Practices for Troubleshooting
- Always validate network reachability first (ping/traceroute).
- Use Live Logs for GUI confirmation before diving into CLI.
- Enable debug radius authentication only during testing; disable after.
- Maintain consistent shared secrets across all RADIUS clients/targets.
- Document NAS IPs, proxy targets, and policy sets for each endpoint to simplify debugging.
Lab Walkthroughs with Validation – External RADIUS Proxy for Cloud NAC
Lab Objective
- Configure Cisco ISE as a RADIUS Proxy forwarding requests to a Cloud NAC.
- Validate authentication, authorization, and failover.
- Map attributes from cloud NAC to ISE Authorization Profiles.
- Troubleshoot and confirm correct end-to-end behavior.
Lab Devices (VMware/EVE-NG Lab)
| Device | IP Address | Role |
|---|---|---|
| ISE Primary Node | 10.50.1.10 | RADIUS Proxy / Policy Server |
| ISE Secondary Node | 10.50.1.11 | Backup / Backend Authentication |
| Cloud NAC | 10.50.2.20 | Target RADIUS Server |
| WLC | 10.50.1.20 | Wireless Controller forwarding RADIUS requests |
| Access Switch | 10.50.1.5 | Wired 802.1X switch |
| Test Endpoint | DHCP 10.50.1.x | Laptop / mobile for authentication test |
| Admin Workstation | 10.50.1.100 | GUI / CLI monitoring |
Step 1 – Configure RADIUS Target in ISE
- Login to ISE GUI → Administration → Network Resources → RADIUS Targets → Add.
- Configure:
- Name:
CloudNAC-Radius - IP:
10.50.2.20 - Auth Port:
1812, Acct Port:1813 - Shared Secret:
CloudSecret123 - Retry: 3, Timeout: 5s
- Name:
Validation:
- GUI: Click Test Connection → should succeed
- CLI:
ping 10.50.2.20 show radius server group CloudNAC-Radius
Step 2 – Configure Network Device in ISE
- Add WLC / Switch: Administration → Network Resources → Network Devices → Add
- IP:
10.50.1.20, Shared Secret:WLCSecret123 - Configure device to forward RADIUS requests to ISE
Validation:
- GUI: Operations → RADIUS Live Logs → see requests from NAS
- CLI:
debug radius authentication show radius statistics
Step 3 – Create Policy Set for RADIUS Proxy
- Policy → Policy Sets → Add:
Cloud NAC Proxy Policy - Condition: NAS IP = WLC IP
- Authentication Policy: Forward to
CloudNAC-Radius - Authorization Policy: Map Cloud NAC attributes to ISE Authorization Profiles (e.g., VLAN, ACL)
Validation:
- GUI: Operations → RADIUS Live Logs →
Proxy Target = CloudNAC-Radius - CLI:
show authentication sessions show radius statistics
- Expected: Access-Accept, correct VLAN/ACL applied
Step 4 – Test Authentication with Wired / Wireless Endpoint
- Connect test laptop/mobile to SSID / wired port
- Observe 802.1X or captive portal authentication flow
Validation:
- GUI: Operations → RADIUS Live Logs → confirm
Proxy Target = CloudNAC-Radius - Authorization Profile applied (VLAN / ACL)
- CLI:
show authentication sessions debug radius authentication
Step 5 – Test Failover / Redundancy
- Add secondary RADIUS Target →
CloudNAC-Secondary - Configure Target Group: Primary =
CloudNAC-Radius, Secondary =CloudNAC-Secondary - Policy Set → Authentication → Use Target Group
- Simulate primary failure (shutdown primary cloud NAC or block 1812/1813)
- Authenticate test client
Validation:
- GUI: Live Logs →
Proxy Target = CloudNAC-Secondary - CLI:
debug radius authentication→ observe request forwarded to secondary - Expected: Access-Accept returned without user impact
Step 6 – Attribute Mapping Validation
- Ensure cloud NAC sends user roles / VLAN / ACL in RADIUS response
- ISE Authorization Policy → maps these attributes to Authorization Profiles
- Test multiple users/groups
Validation:
- GUI: Live Logs → check Authorization Profile applied for each user
- CLI:
show authentication sessions detail
- Expected: Correct VLAN / ACL assigned per cloud NAC attributes
Step 7 – Troubleshooting Common Scenarios
| Scenario | Validation Steps | CLI / GUI |
|---|---|---|
| Access-Reject | Check shared secret, authentication method | debug radius authentication, Live Logs |
| No Proxy Forward | Check NAS IP / Policy Set match | GUI Policy Set conditions, show authentication sessions |
| Failover not working | Check Target Group config, retry / timeout | show radius server group, Live Logs |
| Attribute mapping incorrect | Verify Cloud NAC attributes and ISE mapping | show authentication sessions detail, Authorization Profile |
Step 8 – End-to-End Lab Summary
- Client authenticates via NAS → forwarded by ISE Proxy → Cloud NAC
- Cloud NAC returns Access-Accept + attributes → ISE applies Authorization Profile
- Failover ensures uninterrupted access if primary NAC unavailable
- All authentication sessions and authorization decisions logged in GUI & CLI
Checklist for Validation:
- RADIUS Target connection tested
- Policy Set conditions verified
- Proxy forwarding working (Live Logs / CLI)
- Attribute mapping correct
- Failover tested
- End-to-end authentication successful
Expert Level Use Cases – Step-by-Step Mapping + Validation
Use Case 1: BYOD / Guest Wi-Fi Authentication via Cloud NAC
Objective: Authenticate guest/BYOD users using cloud NAC while ISE acts as a secure RADIUS proxy.
Step-by-Step Implementation:
- Step 1 – Configure Guest SSID on WLC / Access Switch
- GUI: WLC → WLANs → Create SSID → Security → 802.1X with RADIUS server pointing to ISE.
- CLI (WLC):
config wlan create 10 GuestSSID config wlan security wpa akm 802.1X 10 enable config wlan radius add 10 10.50.1.10 1812 CloudSecret123
- Step 2 – Configure ISE as RADIUS Proxy
- Administration → Network Resources → RADIUS Targets → Add
CloudNAC-Radius - Set authentication port
1812, shared secret, retry, timeout.
- Administration → Network Resources → RADIUS Targets → Add
- Step 3 – Configure Policy Set for Guest SSID
- Policy → Policy Sets → Add → Condition:
NAS-IP = WLC IP - Authentication Policy: Forward to
CloudNAC-Radius - Authorization Policy: Map roles returned by Cloud NAC to VLAN or ACL profiles.
- Policy → Policy Sets → Add → Condition:
- Step 4 – Test Endpoint
- Connect laptop/mobile to GuestSSID.
- Validation (GUI): ISE → Operations → RADIUS Live Logs →
Proxy Target = CloudNAC-Radius - Validation (CLI):
debug radius authentication show radius statistics show authentication sessions - Expected Result: Access-Accept from cloud NAC, VLAN/ACL applied as per returned attributes.
Use Case 2: Multi-Region NAC Integration with ISE Proxy
Objective: Route authentication requests to the nearest cloud NAC based on NAS location for low latency.
Step-by-Step Implementation:
- Step 1 – Add Multiple RADIUS Targets in ISE
- GUI: Administration → Network Resources → RADIUS Targets
- Target1:
CloudNAC-East, Target2:CloudNAC-West - Shared secrets & ports configured identically.
- Step 2 – Configure Proxy Target Groups
- Administration → Network Resources → RADIUS Target Groups → Add
- Group Name:
CloudNAC-Regional→ Add both targets - Set Primary = East, Secondary = West
- Step 3 – Policy Set Mapping
- Policy → Policy Sets → Conditions:
- NAS-IP range East → Forward to
CloudNAC-East - NAS-IP range West → Forward to
CloudNAC-West
- NAS-IP range East → Forward to
- Authentication: Use above proxy targets
- Policy → Policy Sets → Conditions:
- Step 4 – Validate
- Connect endpoint from “East” region network
- GUI: Live Logs →
Proxy Target = CloudNAC-East - CLI:
debug radius authentication show radius statistics - Expected Result: Authentication forwarded to regional NAC; Authorization attributes applied.
Use Case 3: High Availability / Failover Scenario
Objective: Ensure authentication continuity if primary cloud NAC is unavailable.
Step-by-Step Implementation:
- Step 1 – Configure Secondary RADIUS Target
- RADIUS Target → Add
CloudNAC-Secondary - Set retry & timeout
- RADIUS Target → Add
- Step 2 – Add to Proxy Target Group
- Target Group → Primary =
CloudNAC-Primary, Secondary =CloudNAC-Secondary
- Target Group → Primary =
- Step 3 – Policy Set
- Use same Policy Set → Authentication → Forward to
CloudNAC-Primary(with fallback to secondary)
- Use same Policy Set → Authentication → Forward to
- Step 4 – Simulate Failover
- Bring down primary cloud NAC (
shutdownor firewall block 1812/1813) - Connect test client to SSID
- Bring down primary cloud NAC (
- Step 5 – Validation
- GUI: Operations → RADIUS Live Logs →
Proxy Target = CloudNAC-Secondary - CLI:
debug radius authentication show radius statistics - Expected Result: Access-Accept from secondary target; seamless failover without user impact.
- GUI: Operations → RADIUS Live Logs →
Use Case 4: Attribute-Based Authorization from Cloud NAC
Objective: Apply VLAN, ACL, or role policies returned from cloud NAC via RADIUS proxy.
Step-by-Step Implementation:
- Step 1 – Create Authorization Profiles in ISE
- GUI: Policy → Policy Elements → Results → Authorization → Add Profile
- Example: VLAN 200 for contractors, ACL
Guest-ACLfor guests
- Step 2 – Policy Set Mapping
- Authorization Policy → Condition:
ExternalGroup = CloudNAC-Contractors→ Apply VLAN 200 - Condition:
ExternalGroup = CloudNAC-Guests→ Apply ACLGuest-ACL
- Authorization Policy → Condition:
- Step 3 – Validate
- Connect test client belonging to each group
- GUI: Live Logs → Verify
Authorization Profile Applied - CLI:
show authentication sessions show radius statistics - Expected Result: User assigned correct VLAN / ACL based on cloud NAC attributes.
Use Case 5: Guest BYOD with Multi-Factor Authentication (Cloud NAC)
Objective: Cloud NAC enforces MFA for guest devices; ISE proxy forwards attributes.
Step-by-Step Implementation:
- Step 1 – Enable MFA on Cloud NAC
- Cloud Portal → Enable MFA for guest users
- Step 2 – Configure ISE Proxy
- Forward 802.1X requests to Cloud NAC proxy target
- Step 3 – Test Authentication
- Connect client → cloud NAC prompts for MFA
- After successful MFA, access allowed
- Step 4 – Validate
- GUI: ISE Live Logs →
Proxy Target = CloudNAC,Access-Accept - CLI:
debug radius authentication→ see MFA attribute returned
- GUI: ISE Live Logs →
Each use case provides:
- Step-by-step mapping: NAS → ISE Proxy → Cloud NAC → Authorization
- Validation: GUI Live Logs, CLI commands, expected outcome
- Notes: Failover, attribute handling, MFA integration
FAQs – External RADIUS Proxy for Cloud NAC
1. Q: Why use an external RADIUS proxy instead of direct client-to-cloud NAC authentication?
A:
- Security: Keeps internal ISE/NAC servers hidden from the internet.
- Policy centralization: ISE enforces consistent policies across multiple NAC targets.
- Logging & Auditing: Centralized authentication and authorization logging.
- Scalability: Supports multiple cloud NACs, regions, or backup targets.
- Validation:
- GUI: Live Logs → authentication source shows
Proxy Target - CLI:
show authentication sessions,debug radius authentication
- GUI: Live Logs → authentication source shows
2. Q: How do I validate that RADIUS requests are being correctly proxied?
A:
- GUI: Operations → RADIUS Live Logs → verify
Proxy Target = CloudNAC-Radius - CLI:
debug radius authentication show authentication sessions show radius statistics
- Expected: Access-Accept returned from cloud NAC, correct attributes applied.
3. Q: What causes “Access-Reject” from cloud NAC through the proxy?
A:
- Common causes:
- Shared secret mismatch
- Wrong authentication method (EAP-TLS, PEAP, etc.)
- Cloud NAC user not provisioned or group mismatch
- Validation: Live Logs → check failure reason; CLI:
debug radius authentication
4. Q: How can I test failover if the primary cloud NAC is down?
A:
- Add secondary RADIUS target in ISE → configure target group with primary/secondary
- Block primary (firewall/shutdown)
- Authenticate test client
- Validation: Live Logs →
Proxy Target = CloudNAC-Secondary; CLI:debug radius authentication
5. Q: Can I map cloud NAC user attributes to ISE Authorization Profiles?
A:
- Yes. Example attributes: VLAN assignment, ACLs, role/group info.
- Steps:
- Authorization Policy → Condition:
ExternalGroup = CloudNAC-Group - Apply Authorization Profile (VLAN, ACL)
- Authorization Policy → Condition:
- Validation: Live Logs → Authorization Profile applied; CLI:
show authentication sessions detail
6. Q: How do I troubleshoot “No RADIUS response received” errors?
A:
- Verify network connectivity (ping/traceroute to cloud NAC)
- Check firewall/NAT rules for UDP 1812/1813
- Validate RADIUS Target configuration (IP, ports, shared secret)
- CLI:
show radius server group CloudNAC-Radius show running-config radius
7. Q: How do I ensure attribute consistency during failover?
A:
- Configure identical Authorization Profiles in ISE mapped to both primary and secondary cloud NAC targets
- Validate: authenticate clients after failover → check VLAN/ACL applied
- GUI: Live Logs → Authorization Profile field
- CLI:
show authentication sessions detail
8. Q: Can I use ISE RADIUS proxy for both wired and wireless clients?
A:
- Yes. Configure NAS devices (switches, WLC) → point to ISE → Policy Set uses Proxy Target
- Validation: Test wired 802.1X + wireless SSID connections → check Live Logs / CLI
9. Q: How do I debug attribute mapping issues when cloud NAC returns unexpected values?
A:
- Steps:
- Capture RADIUS response from cloud NAC (Live Logs → Attributes)
- Verify Authorization Policy in ISE maps the correct attribute → Authorization Profile
- Adjust policy conditions if necessary
- CLI:
show authentication sessions detail debug radius authentication
10. Q: What are best practices for external RADIUS proxy deployment?
A:
- Keep shared secrets synchronized across NAS/Ise/cloud NAC
- Test connectivity to all targets before production
- Use target groups with failover for redundancy
- Monitor Live Logs and CLI debug during deployment
- Validate attribute mapping for VLANs, ACLs, and roles
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- External RADIUS proxy allows secure, scalable, and policy-consistent NAC integration with cloud services.
- Always validate flows using Live Logs and CLI debugging.
- Configure failover targets for high availability.
- Expert use cases include BYOD, guest Wi-Fi, multi-region NAC, and hybrid authentication flows.
Upgrade Your Skills – Start Today
For full Cisco ISE Mastery, join my 4-month instructor-led course, covering cloud NAC, RADIUS proxies, Azure AD integration, guest portals, BYOD flows, and automation. Access labs, scripts, and detailed workbooks.
Fast-Track to Cisco ISE Mastery Pro
Subscribe to Network Journey on YouTube for tutorials and live demonstrations.
Join the training here and take your first step towards becoming a CCIE Security expert.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![Network Design: High Availability vs Load Balancing – Know When to Choose What? [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/Network-Design_High-Availability-vs-Load-Balancing-–-Know-When-to-Choose-What_networkjourney.png)

