ACLs: Named vs Numbered – Which One Should You Use? [CCNP ENTERPRISE]
Access Control Lists (ACLs) are among the first tools you reach for when you want to secure or control traffic. But when it comes to Named vs Numbered ACLs, many learners (and even working professionals) hesitate — unsure which one to use, when, and why.
Let me take you back to my first real-world ACL troubleshooting scenario — a production router, a messy numbered ACL with no comments, and a lot of guesswork. That was the moment I realized: choosing the right type of ACL matters not just for function, but for manageability too.
In this article, we’ll decode the differences, explore real-world usage, and do a hands-on lab in EVE-NG. Let’s go!
Table of Contents
Theory in Brief: What are ACLs?
Access Control Lists (ACLs) are used in networking to control the flow of packets. Think of them as filters placed on interfaces that allow or deny traffic based on IP addresses, protocols, ports, or other parameters.
ACLs come in two primary types:
- Numbered ACLs: Identified by a numeric value (like 1–99, 100–199, etc.)
- Named ACLs: Identified by a string name you define (like “BLOCK-WEB” or “PERMIT-ADMIN”)
Both do the same job — but with different flexibility and management ease.
Why Compare Named vs Numbered?
Numbered ACLs are quick and simple but rigid.
Named ACLs are more readable, editable, and scalable — especially useful in enterprise networks.
The key use cases include:
- Controlling access between subnets or VLANs
- Permitting or denying specific applications or services (like HTTP, SSH)
- Filtering routing updates (BGP, OSPF, EIGRP)
Comparison: Named vs Numbered ACLs
| Feature | Numbered ACLs | Named ACLs |
|---|---|---|
| Identifier | Number (1–199, 1300–2699, etc.) | User-defined string name |
| Editing | Cannot insert/delete mid-sequence | Supports adding/removing lines |
| IPv6 Support | Not supported | Fully supported |
| Clarity | Harder to understand/debug | Easier to read/maintain |
| Use Case | Small configs, quick tests | Production, enterprise environments |
| Support for remarks | No | Yes |
| Protocol flexibility | Standard/Extended limited by range | Full protocol support |
CLI Commands (Cisco IOS)
| Purpose | Command Example |
|---|---|
| Create Numbered Standard ACL | access-list 10 permit 192.168.1.0 0.0.0.255 |
| Create Numbered Extended ACL | access-list 101 permit tcp any any eq 80 |
| Create Named Standard ACL | ip access-list standard BLOCK-LANpermit 10.0.0.0 0.0.0.255 |
| Create Named Extended ACL | ip access-list extended WEB-FILTERdeny tcp any any eq 80 |
| Add remark to Named ACL | remark Block all HTTP traffic |
| Apply ACL to interface (inbound) | ip access-group 101 in or ip access-group WEB-FILTER in |
| Show ACLs | show access-lists or show ip access-lists |
| Remove ACL from interface | no ip access-group 101 in |
| Remove a line in Named ACL | no 10 (inside ACL config mode) |
Real-World Use Cases
| Scenario | ACL Type | Description |
|---|---|---|
| Block HTTP traffic in Guest VLAN | Named Extended | Easy to read and edit later |
| Allow only specific subnet into DMZ | Numbered Standard | Quick config on a test device |
| Filter BGP updates to peers | Named Extended | Use sequence numbers and remarks |
| IPv6 ACL for data center servers | Named IPv6 ACL | Named ACLs are required for IPv6 |
| Permit SSH access to management IPs only | Named Extended | Precise, clean, and auditable |
EVE-NG Lab – ACLs in Action
Topology:
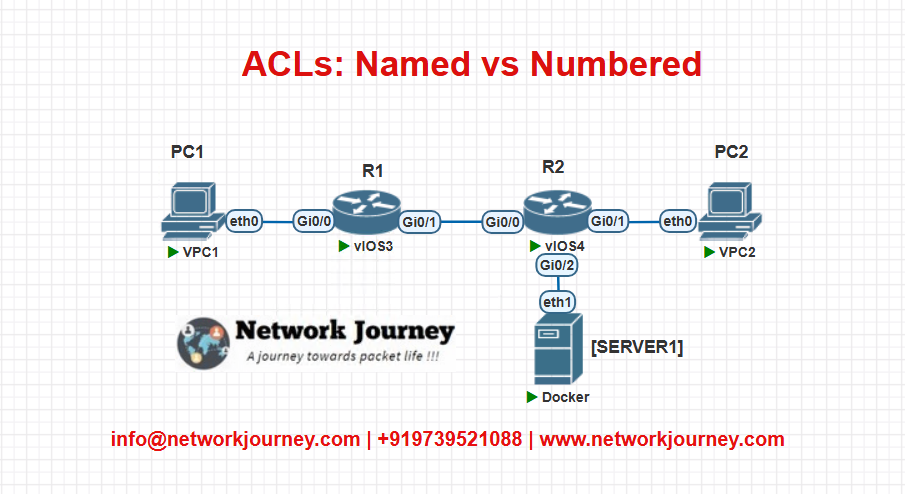
Goal:
- Block HTTP traffic from PC1 to Server1 using both Numbered and Named ACLs on Router R1.
Configuration Steps:
R1 – Using Numbered ACL
interface Gig0/0
description Link to PC1
ip address 192.168.1.1 255.255.255.0
interface Gig0/1
description Link to R2
ip address 10.1.1.1 255.255.255.0
access-list 100 deny tcp any any eq 80
access-list 100 permit ip any any
interface Gig0/0
ip access-group 100 in
R1 – Using Named ACL (Alternative)
ip access-list extended BLOCK-WEB
deny tcp any any eq 80
permit ip any any
interface Gig0/0
ip access-group BLOCK-WEB in
Troubleshooting Tips
| Symptom | Cause | Troubleshooting Command |
|---|---|---|
| ACL not taking effect | Not applied to interface | `show run |
| All traffic blocked | Missing final permit ip any any | Always end with a permit rule |
| Can’t edit existing Numbered ACL | Numbered ACLs are not editable | Recreate the ACL or switch to named ACLs |
| Named ACL sequence not working | Wrong sequence number used | show ip access-lists, check & edit as needed |
| ACL blocking unintended traffic | Rule order mismatch | Reorder or add remarks to improve clarity |
FAQ – ACLs: Named vs Numbered
1. What is the difference between standard and extended ACLs?
Answer:
Standard ACLs filter traffic based only on the source IP address, while extended ACLs allow filtering based on source IP, destination IP, protocol, and port numbers.
Use standard ACLs for basic filtering and extended ACLs for precise traffic control.
2. What are the key differences between named and numbered ACLs?
Answer:
The major differences are:
- Identification: Numbered ACLs use predefined numbers (e.g., 1–199), while named ACLs use custom names.
- Editability: Named ACLs allow inserting/removing entries with sequence numbers.
- Readability: Named ACLs are easier to understand and document with
remark. - IPv6: Only named ACLs support IPv6.
Named ACLs are better suited for enterprise environments.
3. When should I use a numbered ACL instead of a named one?
Answer:
Numbered ACLs are suitable for:
- Quick testing in lab environments
- Small-scale deployments where minimal filtering is needed
- Legacy IOS devices where named ACLs may not be supported
For anything more complex, named ACLs are preferred.
4. Can I modify a specific entry in a numbered ACL?
Answer:
No, numbered ACLs must be completely deleted and recreated to modify individual lines.
Only named ACLs allow editing specific entries using sequence numbers.
5. How do I add or remove rules in a named ACL?
Answer:
Use sequence numbers inside the ACL config mode:
ip access-list extended BLOCK-TELNET
10 deny tcp any any eq 23
20 permit ip any any
To remove a line:
no 10
To insert a new rule:
15 deny tcp 192.168.1.0 0.0.0.255 any eq 80
This flexibility is why named ACLs are preferred in production.
6. Are ACLs stateful or stateless?
Answer:
ACLs on Cisco routers are stateless, meaning they inspect only the packet in one direction.
They do not automatically allow return traffic. For stateful inspection, you need zone-based firewalls or CBAC.
7. What happens if no ACL line matches a packet?
Answer:
There is an implicit deny all at the end of every ACL.
If no rule matches, the traffic is blocked by default. Always include a final permit if you want to allow unmatched traffic, like:
permit ip any any
8. Can I use remarks to document ACLs?
Answer:
Yes, but only in named ACLs.
Use remark to document each rule’s purpose for better readability:
ip access-list extended BLOCK-WEB
remark Deny HTTP from Guest VLAN
deny tcp 192.168.20.0 0.0.0.255 any eq 80
permit ip any any
Remarks are not supported in numbered ACLs.
9. How do I apply ACLs to interfaces?
Answer:
Use the ip access-group command:
interface Gig0/1
ip access-group BLOCK-WEB in
Direction options:
in: Filters packets entering the interfaceout: Filters packets leaving the interface
Always test direction carefully to avoid service disruptions.
10. Do ACLs impact router performance?
Answer:
Minimal, especially on modern hardware. However:
- Large ACLs (hundreds of entries) may increase CPU usage
- Complex ACLs with wildcard matching require more processing
- Always avoid unnecessary ACLs on high-throughput interfaces
Use show processes cpu and show access-lists to monitor impact.
YouTube Link
Watch the Complete CCNP Enterprise: ACLs: Named vs Numbered – Which One Should You Use? Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement ACLs: Named vs Numbered – Which One Should You Use? is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![ACLs: Named vs Numbered – Which One Should You Use? [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-named-numberd.jpg)
![Mastering PortFast, BPDU Guard & Loop Guard: STP Protection Techniques Explained with Lab & CLI. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-PortFast-BPDU-Guard-Loop-Guard_networkjourney.png)
![EIGRP Metric Calculation – Understand the Brain Behind Route Selection. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/EIGRP-Metric-Calculation-–-Understand-the-Brain-Behind-Route-Selection_networkjourney.png)
![Mobility Groups & Roaming – Seamless Wireless in Action [CCNP Enterprise]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Mobility-Groups-Roaming-–-Seamless-Wireless-in-Action-CCNP-Enterprise.png)